Question 81
Which metric should be used when evaluating the effectiveness and scope of a Security Operations Center?
Question 82
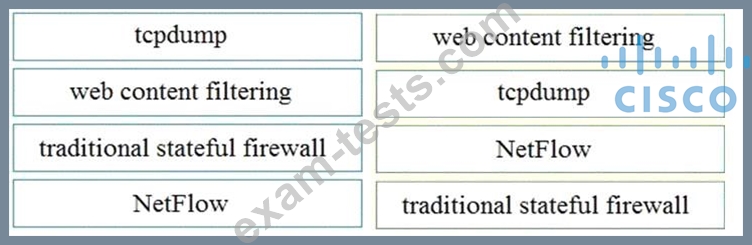
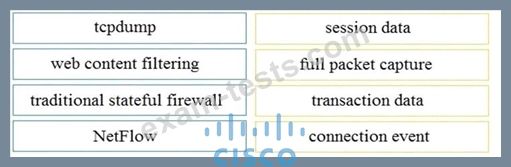
Drag and drop the technology on the left onto the data type the technology provides on the right.

Question 83
An engineer runs a suspicious file in a sandbox analysis tool to see the outcome. The analysis report shows that outbound callouts were made post infection.
Which two pieces of information from the analysis report are needed to investigate the callouts? (Choose two.)
Which two pieces of information from the analysis report are needed to investigate the callouts? (Choose two.)
Question 84
What does cyber attribution identify in an investigation?
Question 85
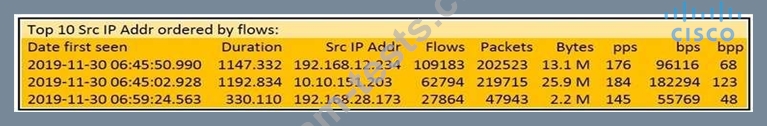
Refer to the exhibit. What information is depicted?
Premium Bundle
Newest 200-201 Exam PDF Dumps shared by BraindumpsPass.com for Helping Passing 200-201 Exam! BraindumpsPass.com now offer the updated 200-201 exam dumps, the BraindumpsPass.com 200-201 exam questions have been updated and answers have been corrected get the latest BraindumpsPass.com 200-201 pdf dumps with Exam Engine here: