Question 66
What does cyber attribution identity in an investigation?
Question 67
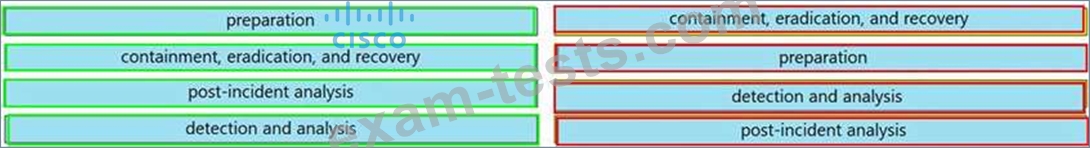
Drag and drop the elements from the left into the correct order for incident handling on the right.
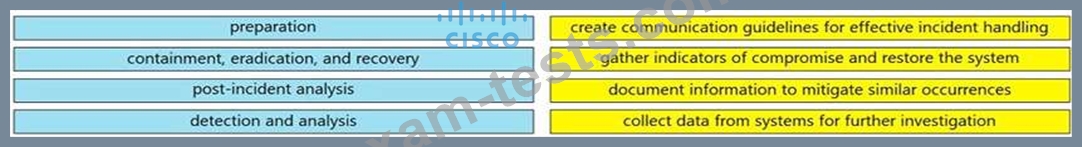

Question 68
Which regex matches only on all lowercase letters?
Question 69
Which security principle requires more than one person is required to perform a critical task?
Question 70
Refer to the exhibit.
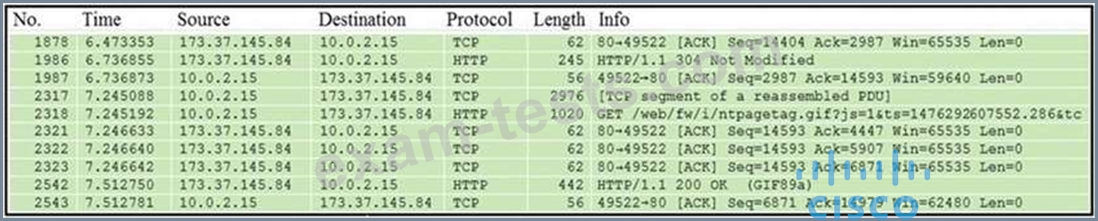
Which packet contains a file that is extractable within Wireshark?

Which packet contains a file that is extractable within Wireshark?