Question 126
What is a benefit of agent-based protection when compared to agentless protection?
Question 127
When trying to evade IDS/IPS devices, which mechanism allows the user to make the data incomprehensible without a specific key, certificate, or password?
Question 128
Refer to the exhibit.
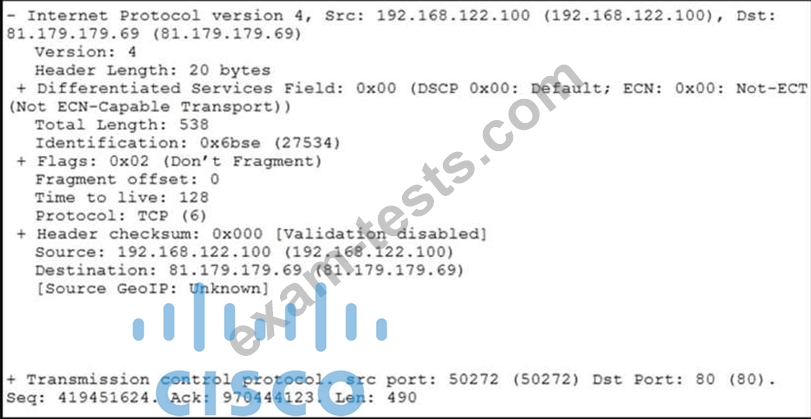
What should be interpreted from this packet capture?

What should be interpreted from this packet capture?

