Question 86
Which evasion technique is a function of ransomware?
Question 87
Which security technology guarantees the integrity and authenticity of all messages transferred to and from a web application?
Question 88
What are the two characteristics of the full packet captures? (Choose two.)
Question 89
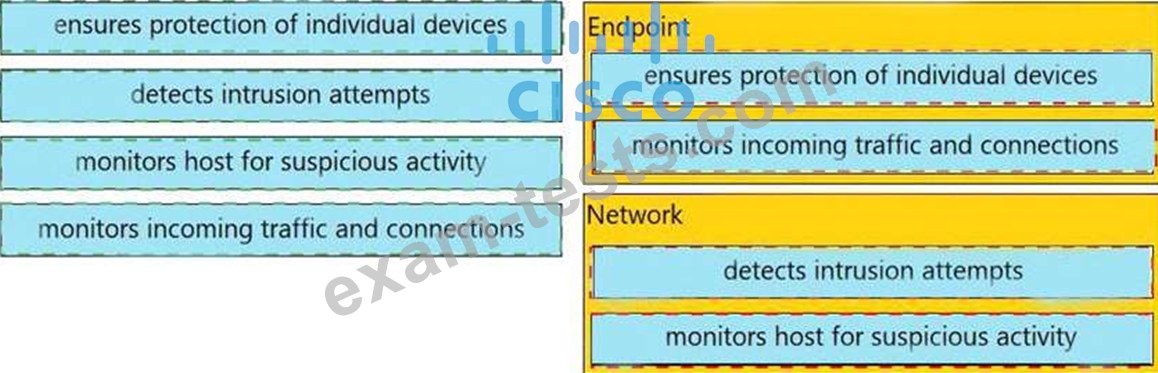
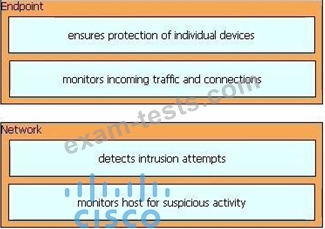
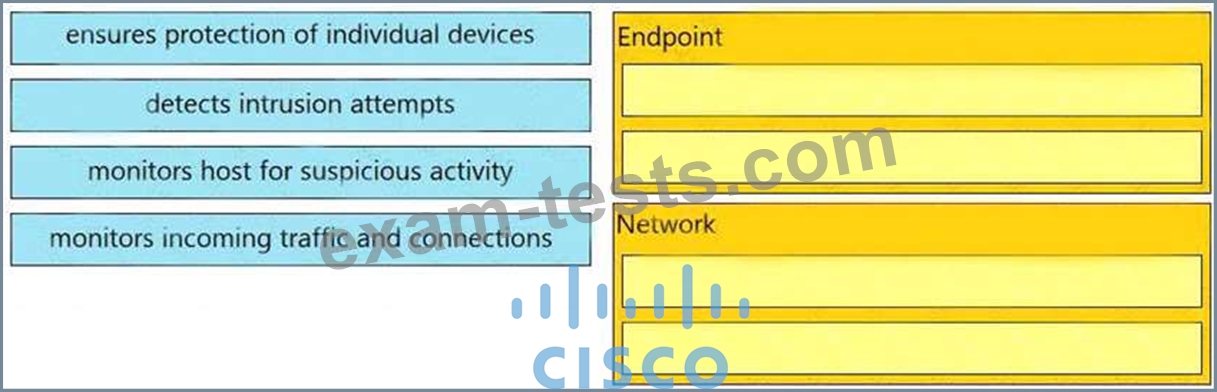
Drag and drop the uses on the left onto the type of security system on the right.

Question 90
Refer to the exhibit.
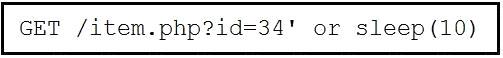
This request was sent to a web application server driven by a database. Which type of web server attack is represented?
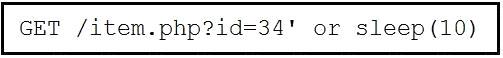
This request was sent to a web application server driven by a database. Which type of web server attack is represented?
Premium Bundle
Newest 200-201 Exam PDF Dumps shared by BraindumpsPass.com for Helping Passing 200-201 Exam! BraindumpsPass.com now offer the updated 200-201 exam dumps, the BraindumpsPass.com 200-201 exam questions have been updated and answers have been corrected get the latest BraindumpsPass.com 200-201 pdf dumps with Exam Engine here: