Question 116
Which action prevents buffer overflow attacks?
Question 117
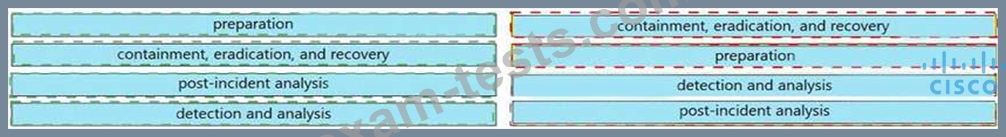
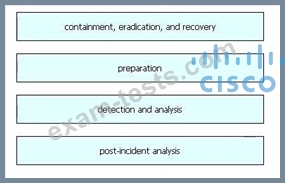
Drag and drop the elements from the left into the correct order for incident handling on the right.


Question 118
A security engineer deploys an enterprise-wide host/endpoint technology for all of the company's corporate PCs. Management requests the engineer to block a selected set of applications on all PCs.
Which technology should be used to accomplish this task?
Which technology should be used to accomplish this task?
Question 119
An analyst received an alert on their desktop computer showing that an attack was successful on the host. After investigating, the analyst discovered that no mitigation action occurred during the attack. What is the reason for this discrepancy?
Question 120

Refer to the exhibit. Which type of log is displayed?
Premium Bundle
Newest 200-201 Exam PDF Dumps shared by BraindumpsPass.com for Helping Passing 200-201 Exam! BraindumpsPass.com now offer the updated 200-201 exam dumps, the BraindumpsPass.com 200-201 exam questions have been updated and answers have been corrected get the latest BraindumpsPass.com 200-201 pdf dumps with Exam Engine here: