Question 61
Which step in the incident response process researches an attacking host through logs in a SIEM?
Question 62
Refer to the exhibit.
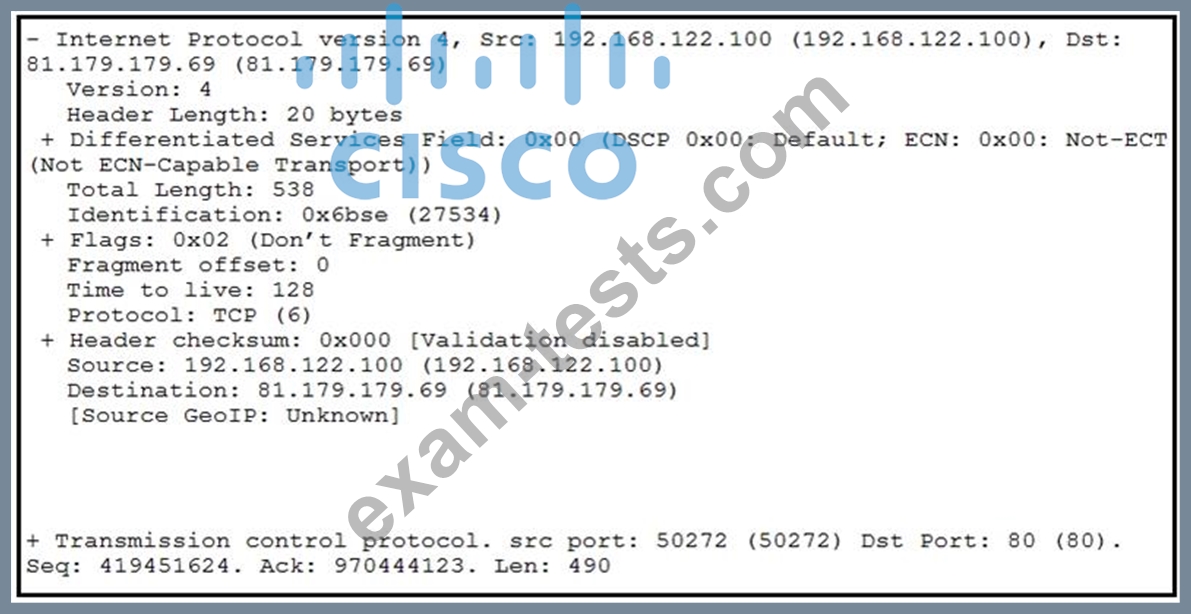
What should be interpreted from this packet capture?

What should be interpreted from this packet capture?
Question 63
What is the impact of false positive alerts on business compared to true positive?
Question 64
Refer to the exhibit.
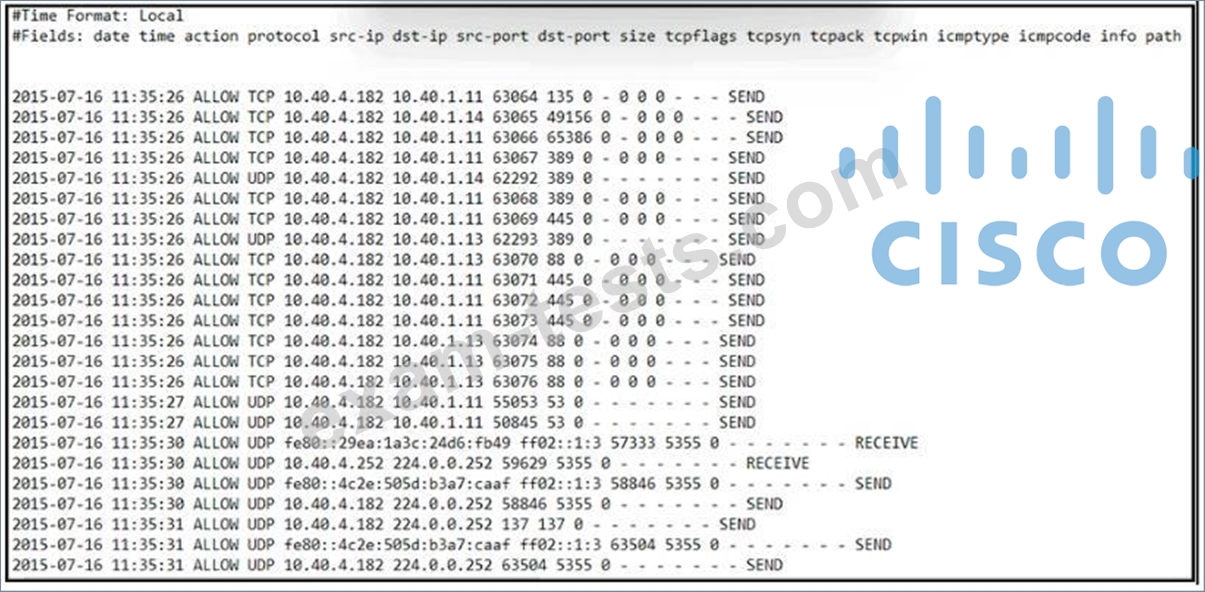
An engineer received an event log file to review. Which technology generated the log?

An engineer received an event log file to review. Which technology generated the log?
Question 65
Which artifact is used to uniquely identify a detected file?
Premium Bundle
Newest 200-201 Exam PDF Dumps shared by BraindumpsPass.com for Helping Passing 200-201 Exam! BraindumpsPass.com now offer the updated 200-201 exam dumps, the BraindumpsPass.com 200-201 exam questions have been updated and answers have been corrected get the latest BraindumpsPass.com 200-201 pdf dumps with Exam Engine here:

