Question 36
Refer to the exhibit.
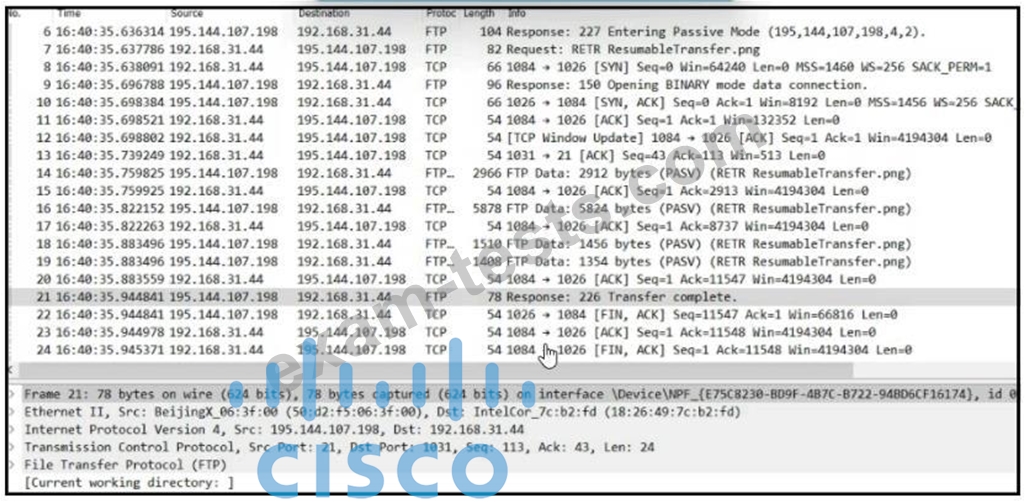
Which frame numbers contain a file that is extractable via TCP stream within Wireshark?

Which frame numbers contain a file that is extractable via TCP stream within Wireshark?
Question 37
An analyst received an alert on their desktop computer showing that an attack was successful on the host.
After investigating, the analyst discovered that no mitigation action occurred during the attack. What is the reason for this discrepancy?
After investigating, the analyst discovered that no mitigation action occurred during the attack. What is the reason for this discrepancy?
Question 38
Which technology should be used to implement a solution that makes routing decisions based on HTTP header, uniform resource identifier, and SSL session ID attributes?
Question 39
Which security monitoring data type requires the largest storage space?
Question 40
What is the relationship between a vulnerability and a threat?

