Question 76
Which security technology guarantees the integrity and authenticity of all messages transferred to and from a web application?
Question 77
Which two components reduce the attack surface on an endpoint? (Choose two.)
Question 78
Refer to the exhibit.

What is occurring within the exhibit?

What is occurring within the exhibit?
Question 79
A malicious file has been identified in a sandbox analysis tool.
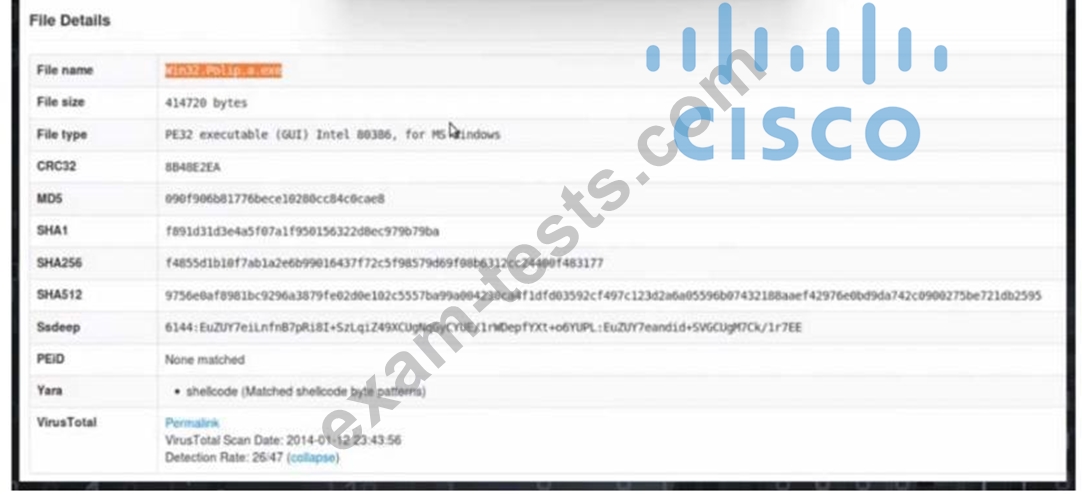
Which piece of information is needed to search for additional downloads of this file by other hosts?

Which piece of information is needed to search for additional downloads of this file by other hosts?
Question 80
At which layer is deep packet inspection investigated on a firewall?

