Question 46
Refer to the exhibit.

Which type of log is displayed?

Which type of log is displayed?
Question 47
A security engineer notices confidential data being exfiltrated to a domain "Ranso4134-mware31-895" address that is attributed to a known advanced persistent threat group The engineer discovers that the activity is part of a real attack and not a network misconfiguration. Which category does this event fall under as defined in the Cyber Kill Chain?
Question 48
Refer to the exhibit.
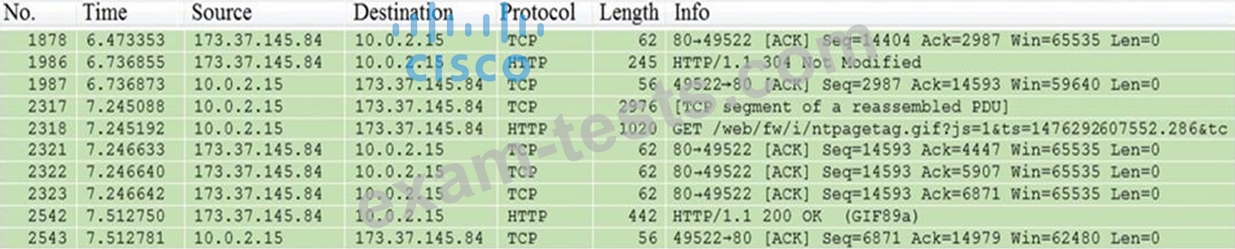
Which packet contains a file that is extractable within Wireshark?

Which packet contains a file that is extractable within Wireshark?
Question 49
A security engineer has a video of a suspect entering a data center that was captured on the same day that files in the same data center were transferred to a competitor.
Which type of evidence is this?
Which type of evidence is this?
Question 50
Which principle is being followed when an analyst gathers information relevant to a security incident to determine the appropriate course of action?

