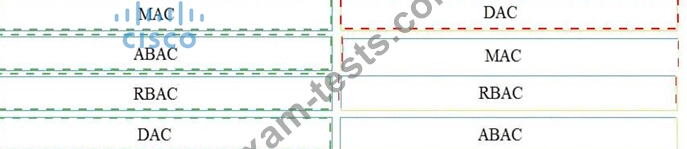
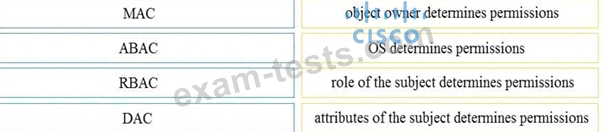
Question 11
Drag and drop the access control models from the left onto the correct descriptions on the right.

Question 12
Which two elements are assets in the role of attribution in an investigation? (Choose two.)
Question 13
What ate two denial-of-service (DoS) attacks? (Choose two)
Question 14
An organization's security team has detected network spikes coming from the internal network. An investigation has concluded that the spike in traffic was from intensive network scanning How should the analyst collect the traffic to isolate the suspicious host?
Question 15
What is the difference between discretionary access control (DAC) and role-based access control (RBAC)?