Question 31
What is the impact of encryption?
Question 32
What is a purpose of a vulnerability management framework?
Question 33
What is a collection of compromised machines that attackers use to carry out a DDoS attack?
Question 34
An engineer needs to have visibility on TCP bandwidth usage, response time, and latency, combined with deep packet inspection to identify unknown software by its network traffic flow. Which two features of Cisco Application Visibility and Control should the engineer use to accomplish this goal? (Choose two.)
Question 35
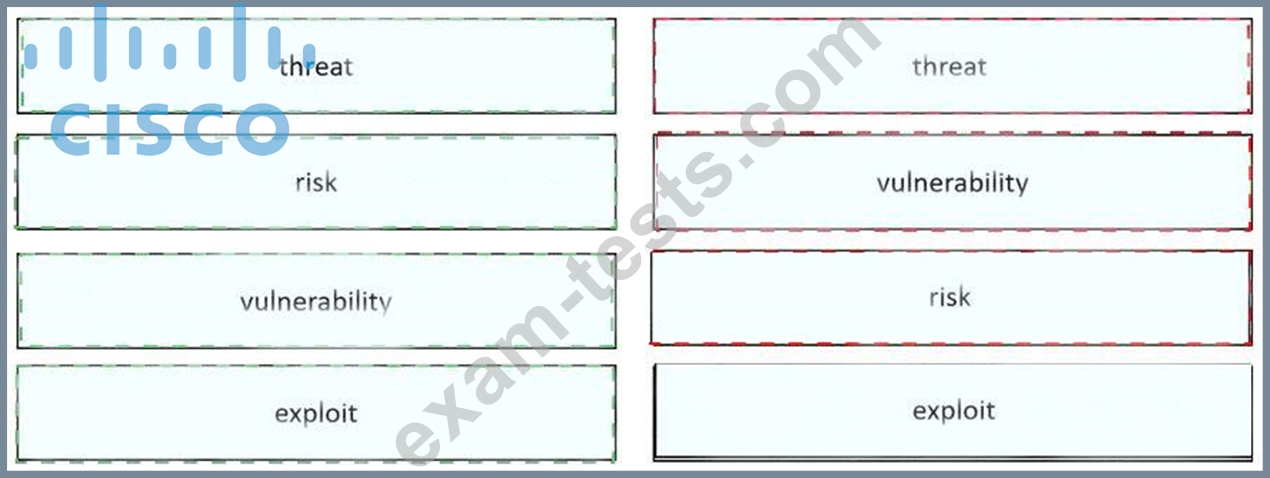
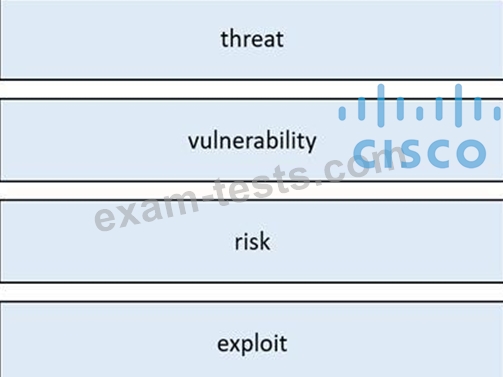
Drag and drop the security concept from the left onto the example of that concept on the right.