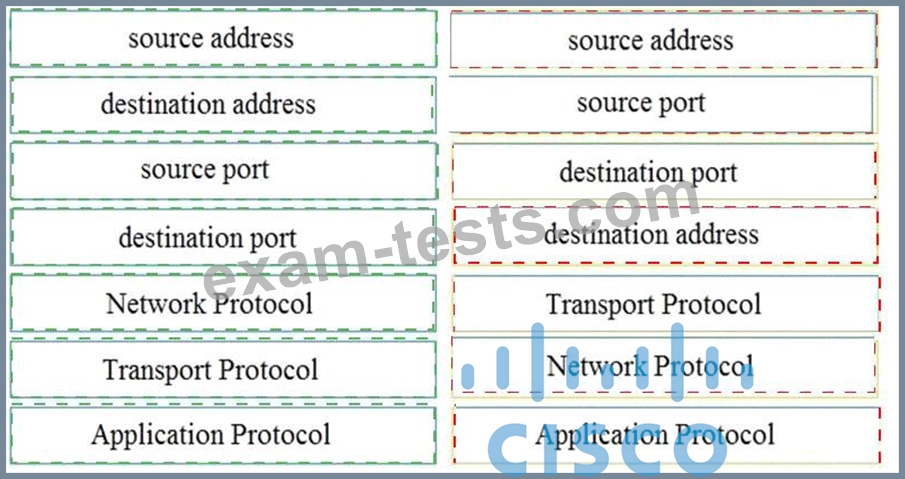
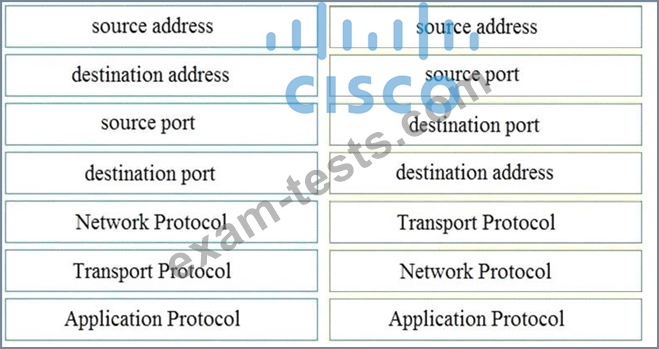
Question 21
A user received an email attachment named "Hr405-report2609-empl094.exe" but did not run it. Which category of the cyber kill chain should be assigned to this type of event?
Question 22
Refer to the exhibit.
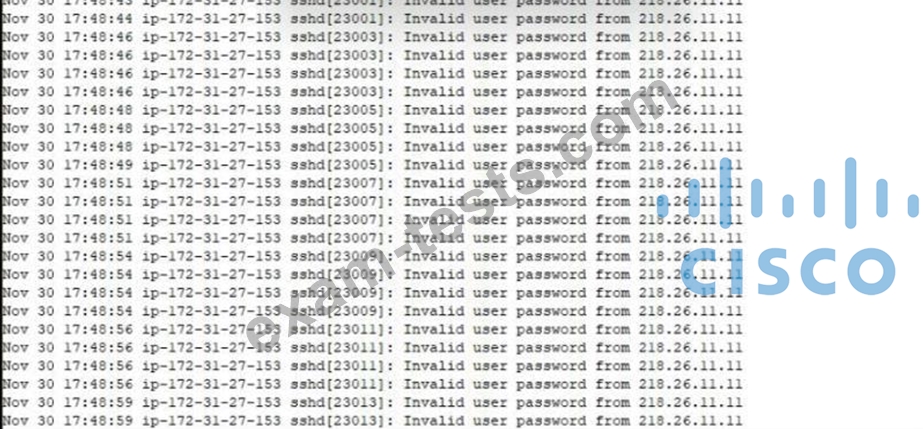
A security analyst is investigating unusual activity from an unknown IP address Which type of evidence is this file1?

A security analyst is investigating unusual activity from an unknown IP address Which type of evidence is this file1?
Question 23
Refer to the exhibit.
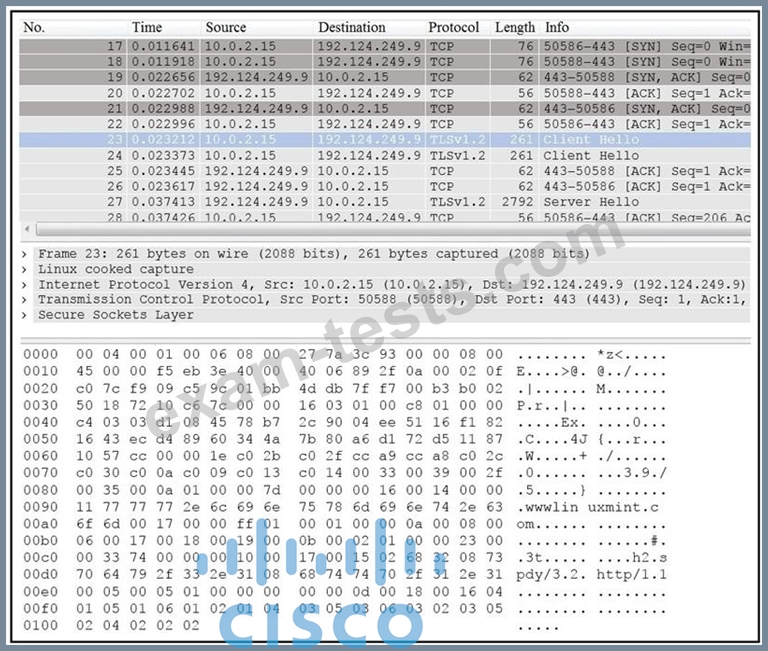
Drag and drop the element name from the left onto the correct piece of the PCAP file on the right.
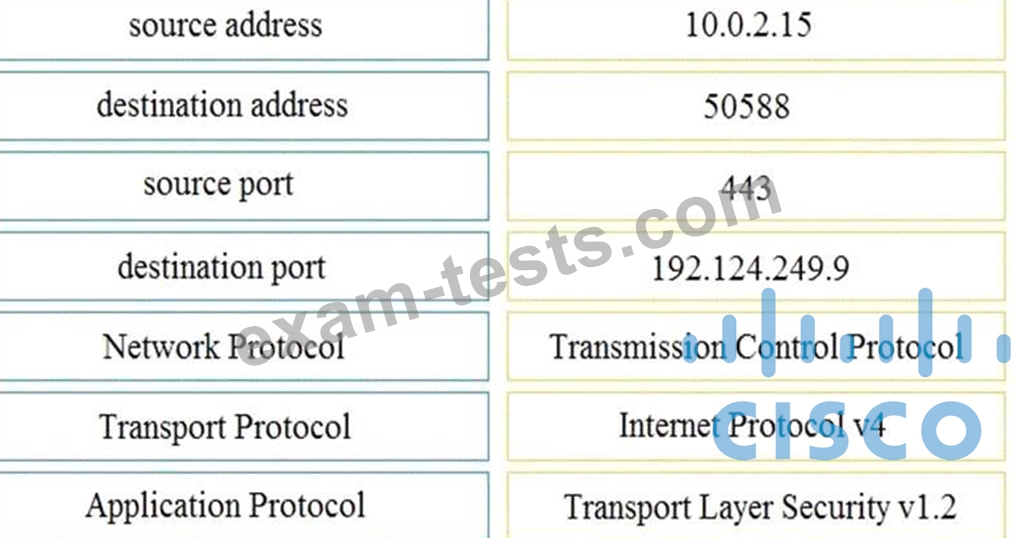

Drag and drop the element name from the left onto the correct piece of the PCAP file on the right.

Question 24
What is the principle of defense-in-depth?
Question 25
An engineer received an alert affecting the degraded performance of a critical server. Analysis showed a heavy CPU and memory load. What is the next step the engineer should take to investigate this resource usage?