Question 81
An analyst discovers that a legitimate security alert has been dismissed.
Which signature caused this impact on network traffic?
Which signature caused this impact on network traffic?
Question 82
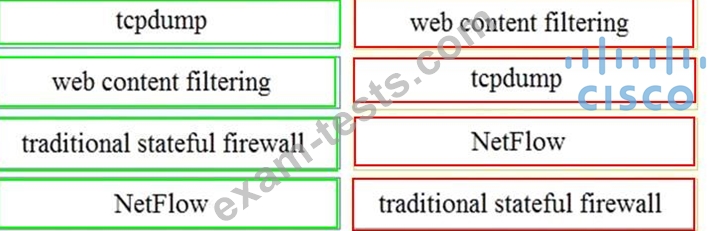
Drag and drop the technology on the left onto the data type the technology provides on the right.


Question 83
An analyst is investigating a host in the network that appears to be communicating to a command and control server on the Internet. After collecting this packet capture, the analyst cannot determine the technique and payload used for the communication.
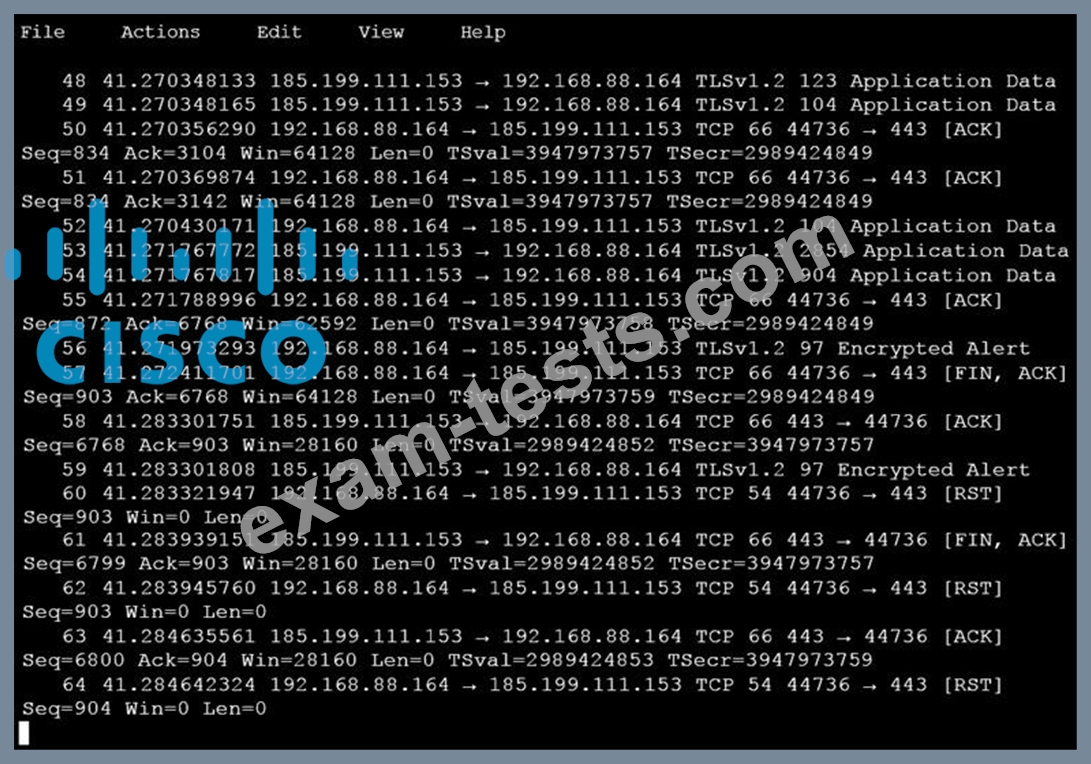
Which obfuscation technique is the attacker using?

Which obfuscation technique is the attacker using?
Question 84
What describes a buffer overflow attack?
Question 85
An investigator is examining a copy of an ISO file that is stored in CDFS format. What type of evidence is this file?
Premium Bundle
Newest 200-201 Exam PDF Dumps shared by BraindumpsPass.com for Helping Passing 200-201 Exam! BraindumpsPass.com now offer the updated 200-201 exam dumps, the BraindumpsPass.com 200-201 exam questions have been updated and answers have been corrected get the latest BraindumpsPass.com 200-201 pdf dumps with Exam Engine here: