Question 101
Refer to the exhibit.
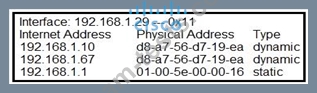
What is occurring in this network?

What is occurring in this network?
Question 102
What describes the concept of data consistently and readily being accessible for legitimate users?
Question 103
Which technology on a host is used to isolate a running application from other applications?
Question 104
Refer to the exhibit.
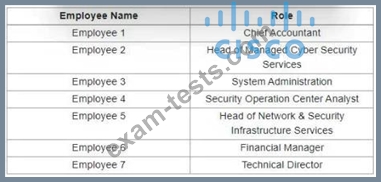
Which stakeholders must be involved when a company workstation is compromised?

Which stakeholders must be involved when a company workstation is compromised?
Question 105
A security analyst notices a sudden surge of incoming traffic and detects unknown packets from unknown senders After further investigation, the analyst learns that customers claim that they cannot access company servers According to NIST SP800-61, in which phase of the incident response process is the analyst?
Premium Bundle
Newest 200-201 Exam PDF Dumps shared by BraindumpsPass.com for Helping Passing 200-201 Exam! BraindumpsPass.com now offer the updated 200-201 exam dumps, the BraindumpsPass.com 200-201 exam questions have been updated and answers have been corrected get the latest BraindumpsPass.com 200-201 pdf dumps with Exam Engine here:

