Question 86
What is the difference between deep packet inspection and stateful inspection?
Question 87
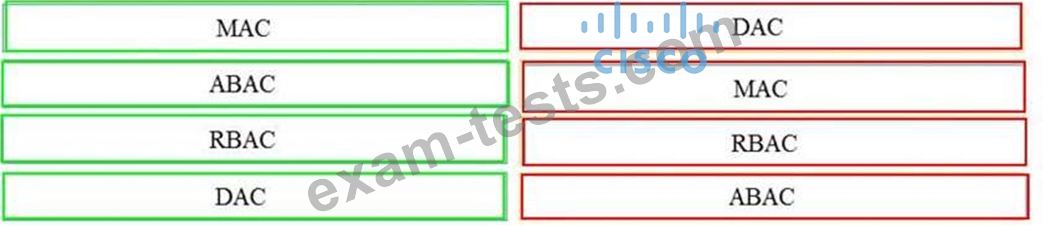
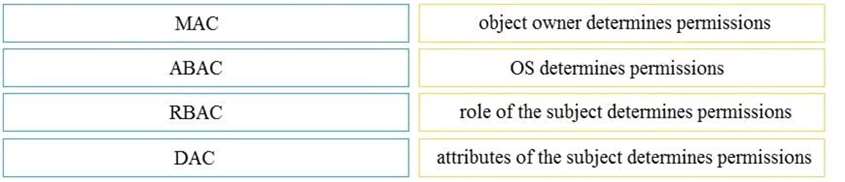
Drag and drop the access control models from the left onto the correct descriptions on the right.

Question 88
Which are two denial-of-service attacks? (Choose two.)
Question 89
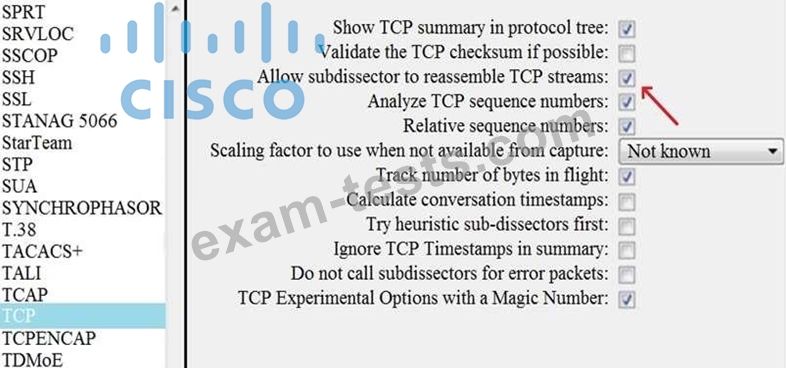
Refer to the exhibit. What is the expected result when the "Allow subdissector to reassemble TCP streams" feature is enabled?
Question 90
Which attack represents the evasion technique of resource exhaustion?