Question 106
Refer to the exhibit.
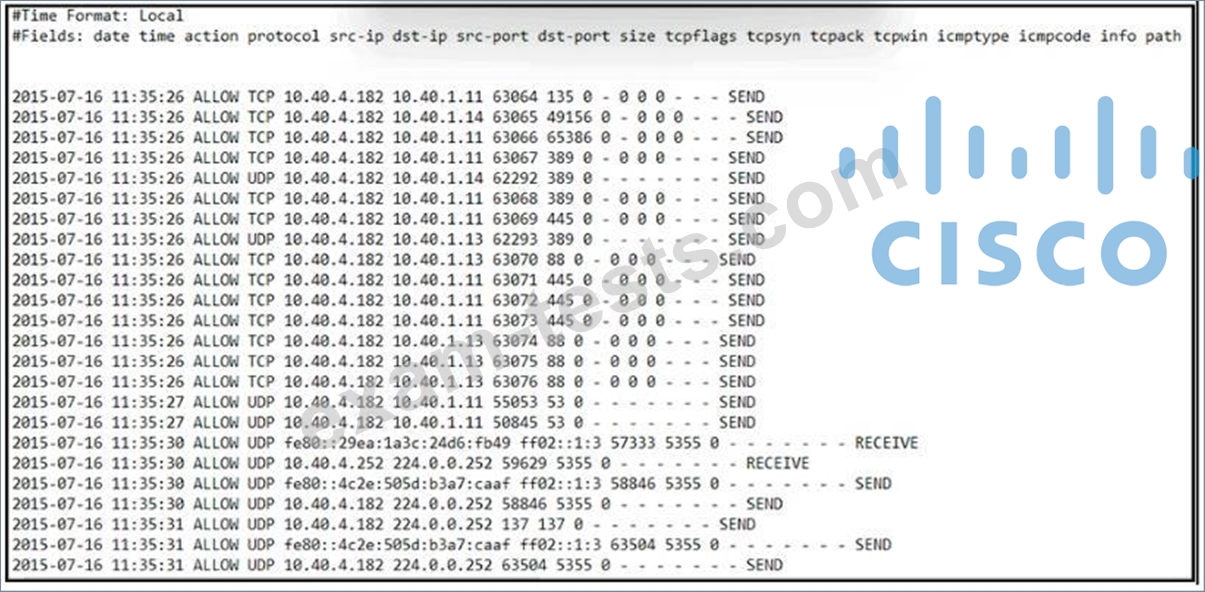
An engineer received an event log file to review. Which technology generated the log?

An engineer received an event log file to review. Which technology generated the log?
Question 107
Refer to the exhibit.
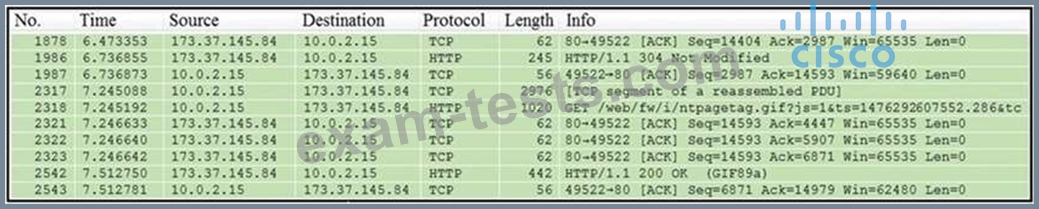
Which packet contains a file that is extractable within Wireshark?

Which packet contains a file that is extractable within Wireshark?
Question 108
A malicious file has been identified in a sandbox analysis tool.
Which piece of information is needed to search for additional downloads of this file by other hosts?
Which piece of information is needed to search for additional downloads of this file by other hosts?
Question 109
Which two elements are assets in the role of attribution in an investigation? (Choose two.)
Question 110
A system administrator is ensuring that specific registry information is accurate.
Which type of configuration information does the HKEY_LOCAL_MACHINE hive contain?
Which type of configuration information does the HKEY_LOCAL_MACHINE hive contain?
Premium Bundle
Newest 200-201 Exam PDF Dumps shared by BraindumpsPass.com for Helping Passing 200-201 Exam! BraindumpsPass.com now offer the updated 200-201 exam dumps, the BraindumpsPass.com 200-201 exam questions have been updated and answers have been corrected get the latest BraindumpsPass.com 200-201 pdf dumps with Exam Engine here:

