Question 116
Refer to the exhibit.

Which component is identifiable in this exhibit?

Which component is identifiable in this exhibit?
Question 117
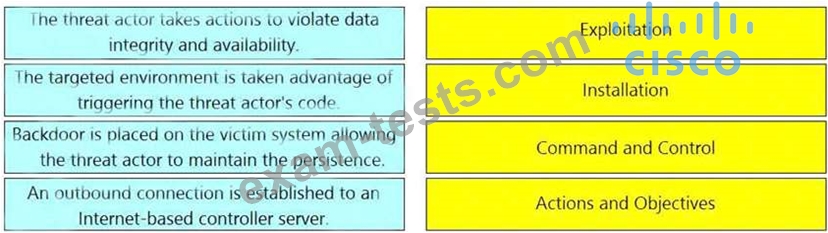
Drag and drop the definition from the left onto the phase on the right to classify intrusion events according to the Cyber Kill Chain model.

Question 118
What is the virtual address space for a Windows process?
Question 119
Refer to the exhibit.
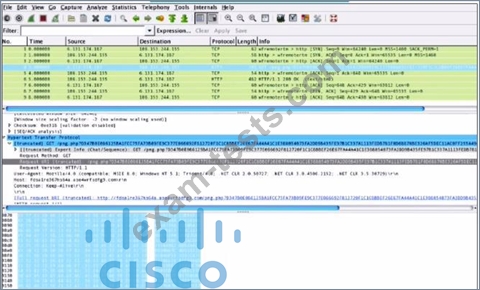
What is shown in this PCAP file?

What is shown in this PCAP file?
Question 120
A SOC analyst is investigating an incident that involves a Linux system that is identifying specific sessions.
Which identifier tracks an active program?
Which identifier tracks an active program?
Premium Bundle
Newest 200-201 Exam PDF Dumps shared by BraindumpsPass.com for Helping Passing 200-201 Exam! BraindumpsPass.com now offer the updated 200-201 exam dumps, the BraindumpsPass.com 200-201 exam questions have been updated and answers have been corrected get the latest BraindumpsPass.com 200-201 pdf dumps with Exam Engine here: