Question 121
An offline audit log contains the source IP address of a session suspected to have exploited a vulnerability resulting in system compromise.
Which kind of evidence is this IP address?
Which kind of evidence is this IP address?
Question 122
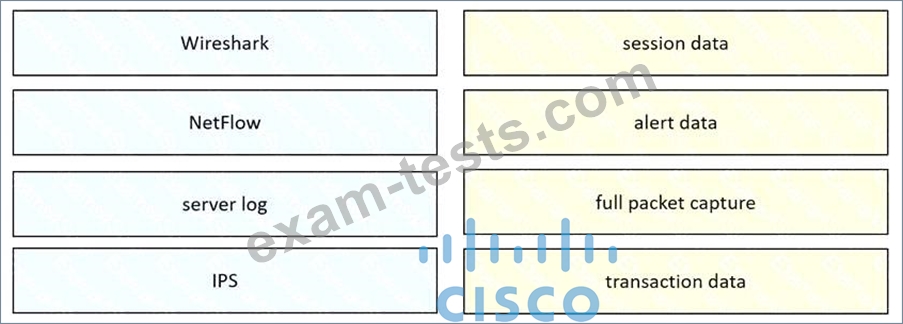
Drag and drop the data source from the left onto the data type on the right.

Question 123
Which data format is the most efficient to build a baseline of traffic seen over an extended period of time?
Question 124
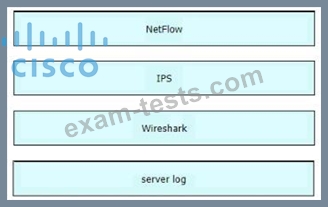
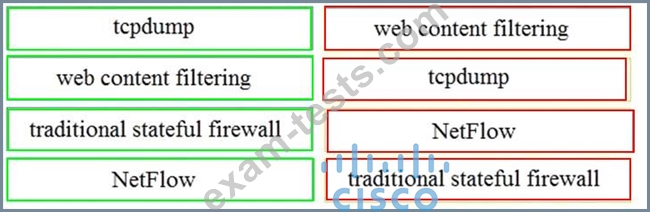
Drag and drop the technology on the left onto the data type the technology provides on the right.


Question 125
What is a purpose of a vulnerability management framework?
Premium Bundle
Newest 200-201 Exam PDF Dumps shared by BraindumpsPass.com for Helping Passing 200-201 Exam! BraindumpsPass.com now offer the updated 200-201 exam dumps, the BraindumpsPass.com 200-201 exam questions have been updated and answers have been corrected get the latest BraindumpsPass.com 200-201 pdf dumps with Exam Engine here: