Question 1
The purpose of a __________ is to deny network access to local area networks and other information assets by unauthorized wireless devices.
Question 2
Which of the following statements is FALSE with respect to Intrusion Detection Systems?
Question 3
Eve is spending her day scanning the library computers. She notices that Alice is using a computer whose port 445 is active and listening. Eve uses the ENUM tool to enumerate Alice machine. From the command prompt, she types the following command.
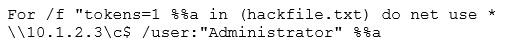
What is Eve trying to do?

What is Eve trying to do?
Question 4
Which cipher encrypts the plain text digit (bit or byte) one by one?
Question 5
Your team has won a contract to infiltrate an organization. The company wants to have the attack be as
realistic as possible; therefore, they did not provide any information besides the company name. What
should be the first step in security testing the client?
realistic as possible; therefore, they did not provide any information besides the company name. What
should be the first step in security testing the client?

