Question 1
Refer to the exhibit.
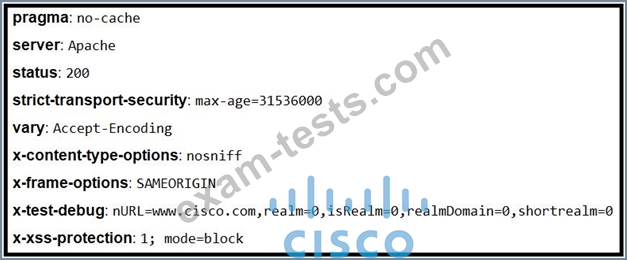
Where is the MIME type that should be followed indicated?

Where is the MIME type that should be followed indicated?
Question 2
An engineer is going through vulnerability triage with company management because of a recent malware outbreak from which 21 affected assets need to be patched or remediated. Management decides not to prioritize fixing the assets and accepts the vulnerabilities. What is the next step the engineer should take?
Question 3
What is a principle of Infrastructure as Code?
Question 4
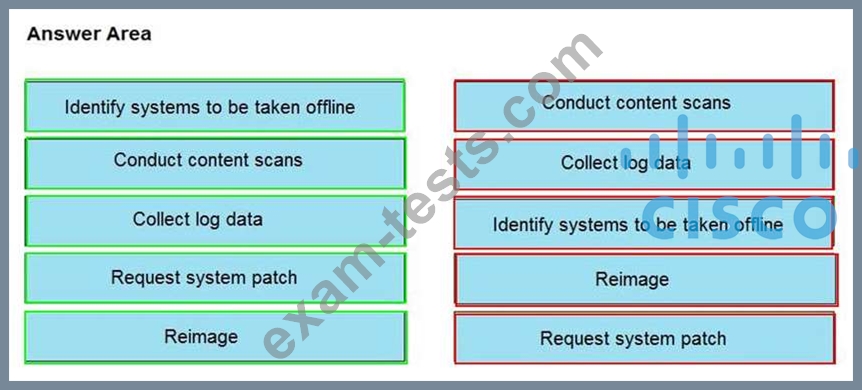
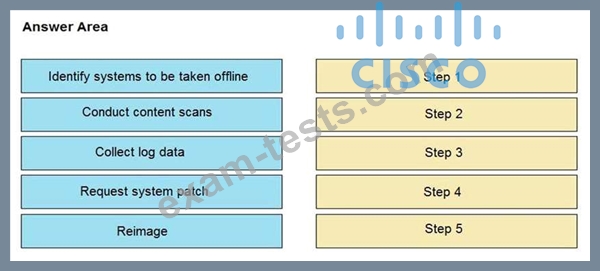
An engineer notices that unauthorized software was installed on the network and discovers that it was installed by a dormant user account. The engineer suspects an escalation of privilege attack and responds to the incident. Drag and drop the activities from the left into the order for the response on the right.

Question 5
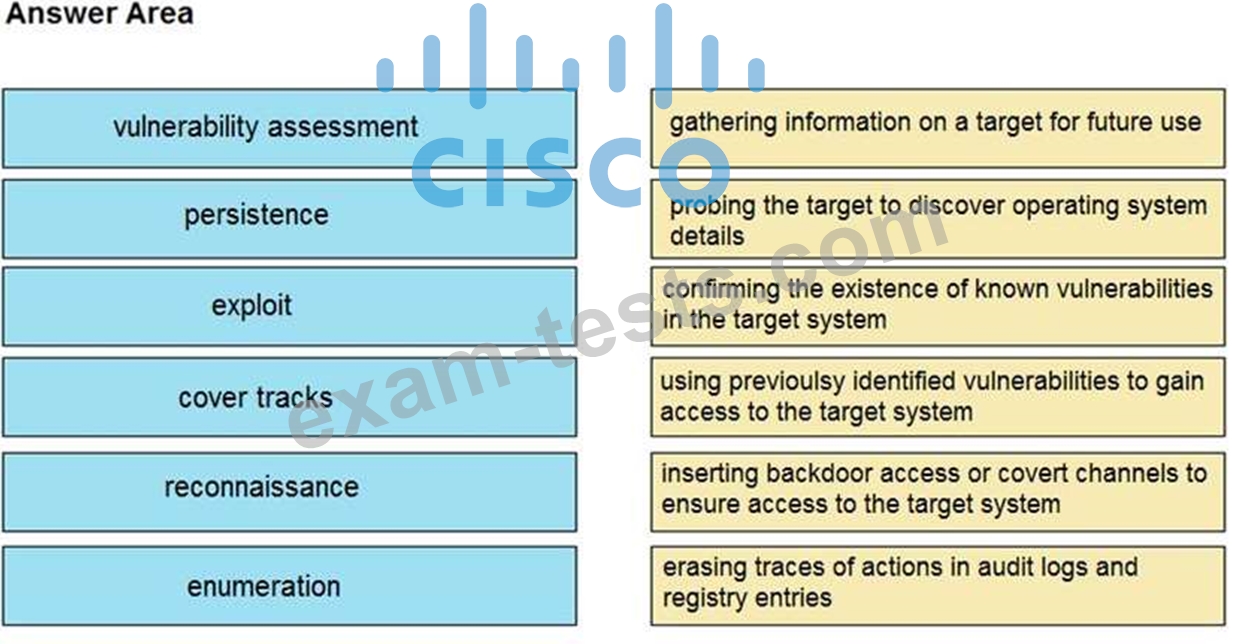
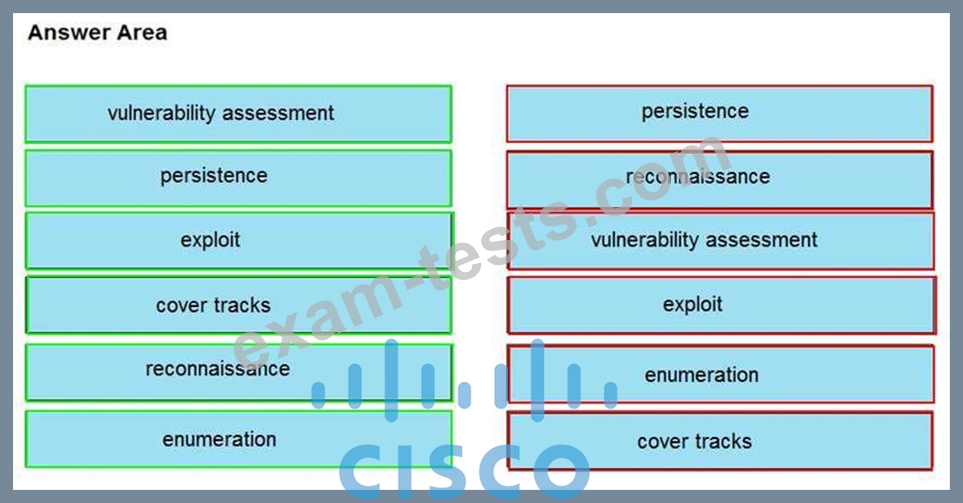
Drag and drop the phases to evaluate the security posture of an asset from the left onto the activity that happens during the phases on the right.