Question 6
How does Wireshark decrypt TLS network traffic?
Question 7
An engineer received multiple reports from users trying to access a company website and instead of landing on the website, they are redirected to a malicious website that asks them to fill in sensitive personal dat a. Which type of attack is occurring?
Question 8
A SIEM tool fires an alert about a VPN connection attempt from an unusual location. The incident response team validates that an attacker has installed a remote access tool on a user's laptop while traveling. The attacker has the user's credentials and is attempting to connect to the network.
What is the next step in handling the incident?
What is the next step in handling the incident?
Question 9
Refer to the exhibit.
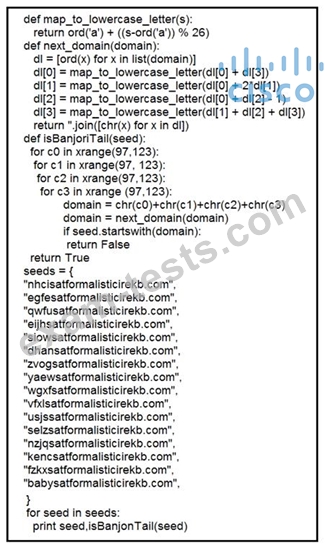
What results from this script?

What results from this script?
Question 10
Refer to the exhibit.
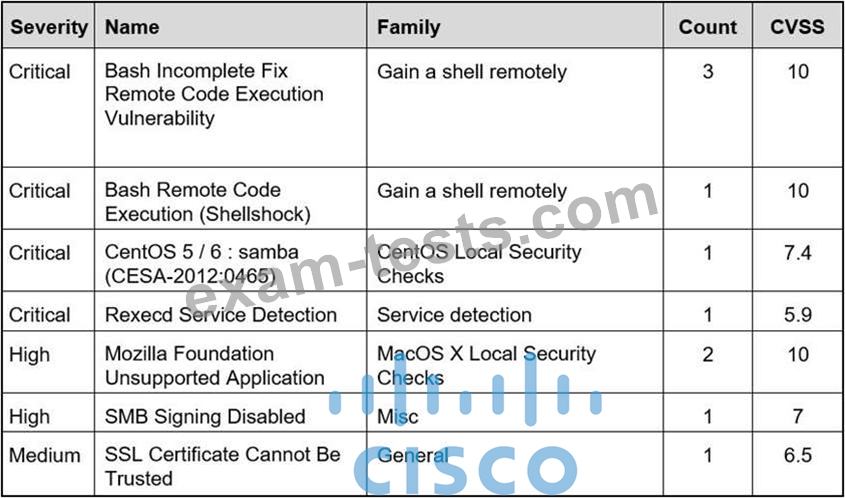
Based on the detected vulnerabilities, what is the next recommended mitigation step?

Based on the detected vulnerabilities, what is the next recommended mitigation step?

