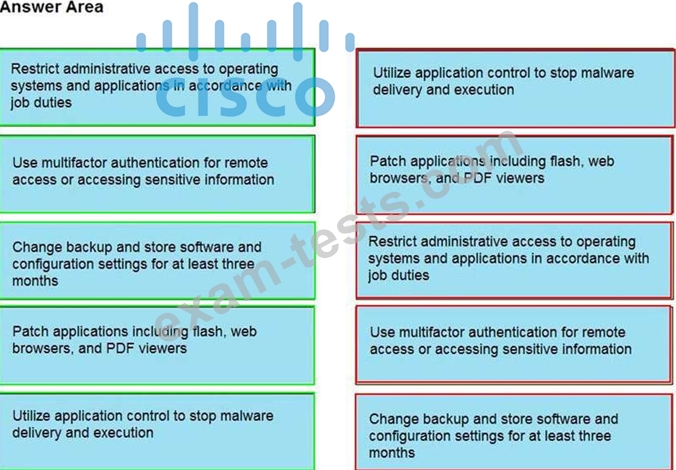
Question 11
Refer to the exhibit.
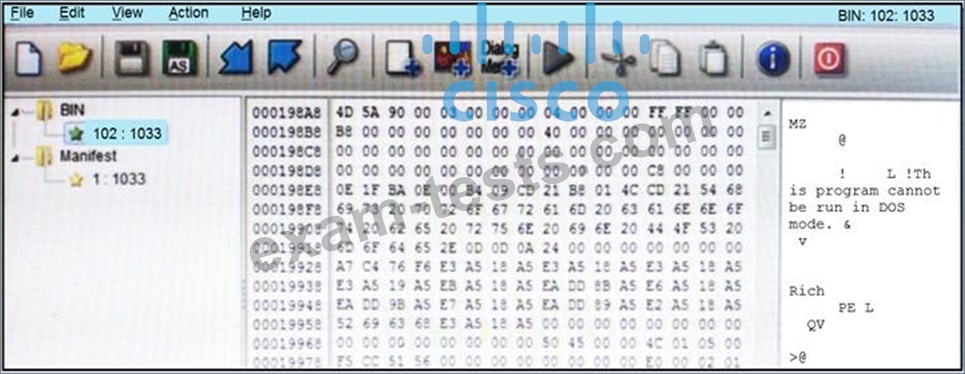
An engineer is reverse engineering a suspicious file by examining its resources. What does this file indicate?

An engineer is reverse engineering a suspicious file by examining its resources. What does this file indicate?
Question 12
Drag and drop the mitigation steps from the left onto the vulnerabilities they mitigate on the right.
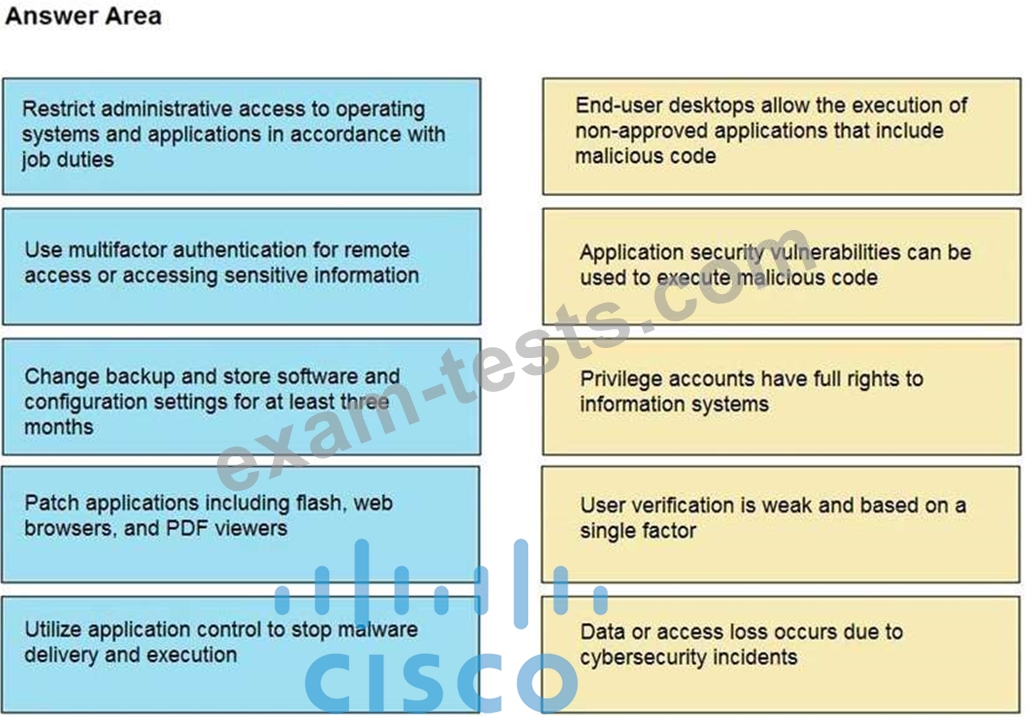

Question 13
Refer to the exhibit.
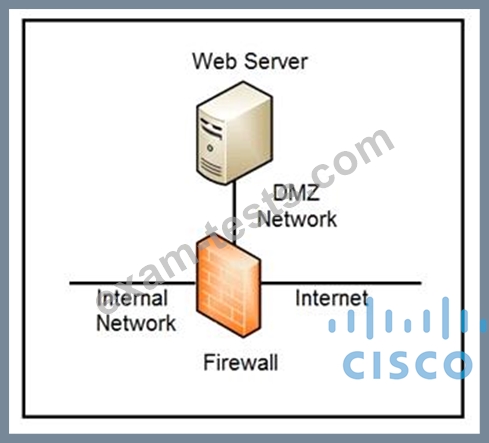
Which two steps mitigate attacks on the webserver from the Internet? (Choose two.)

Which two steps mitigate attacks on the webserver from the Internet? (Choose two.)
Question 14
Employees receive an email from an executive within the organization that summarizes a recent security breach and requests that employees verify their credentials through a provided link. Several employees report the email as suspicious, and a security analyst is investigating the reports. Which two steps should the analyst take to begin this investigation? (Choose two.)
Question 15
A new malware variant is discovered hidden in pirated software that is distributed on the Internet. Executives have asked for an organizational risk assessment. The security officer is given a list of all assets. According to NIST, which two elements are missing to calculate the risk assessment? (Choose two.)