Question 26
Refer to the exhibit.
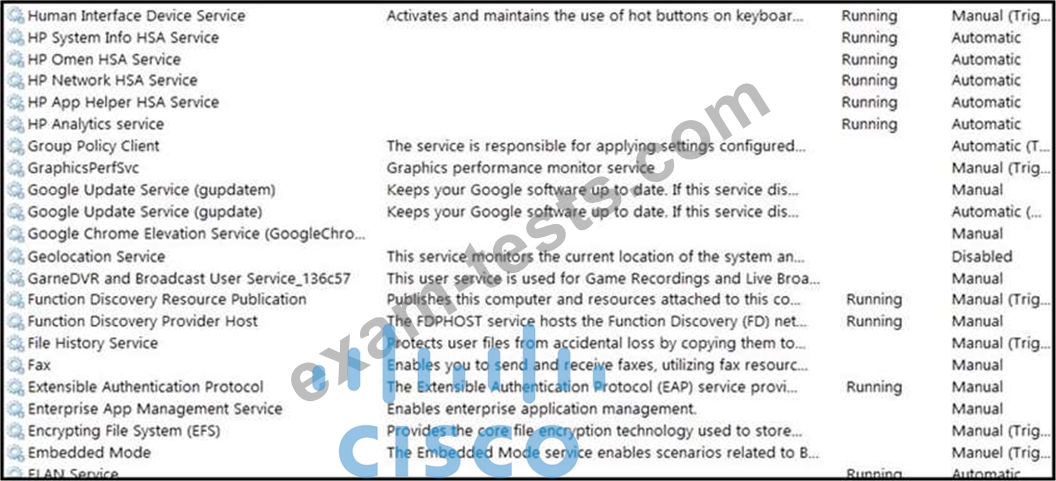
An engineer received multiple reports from employees unable to log into systems with the error: The Group Policy Client service failed to logon - Access is denied. Through further analysis, the engineer discovered several unexpected modifications to system settings. Which type of breach is occurring?

An engineer received multiple reports from employees unable to log into systems with the error: The Group Policy Client service failed to logon - Access is denied. Through further analysis, the engineer discovered several unexpected modifications to system settings. Which type of breach is occurring?
Question 27
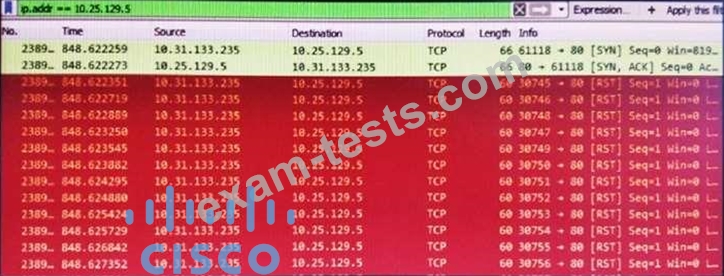
Refer to the exhibit. What is occurring in this packet capture?

Question 28
An organization installed a new application server for IP phones. An automated process fetched user credentials from the Active Directory server, and the application will have access to on-premises and cloud services. Which security threat should be mitigated first?
Question 29
According to GDPR, what should be done with data to ensure its confidentiality, integrity, and availability?
Question 30
Refer to the exhibit.
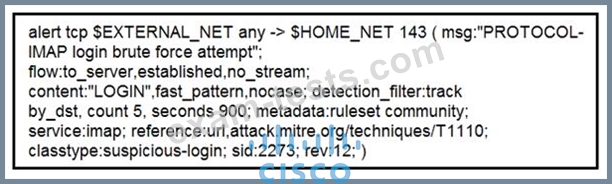
IDS is producing an increased amount of false positive events about brute force attempts on the organization's mail server. How should the Snort rule be modified to improve performance?

IDS is producing an increased amount of false positive events about brute force attempts on the organization's mail server. How should the Snort rule be modified to improve performance?

