Question 46
What is the impact of hardening machine images for deployment?
Question 47
Refer to the exhibit.
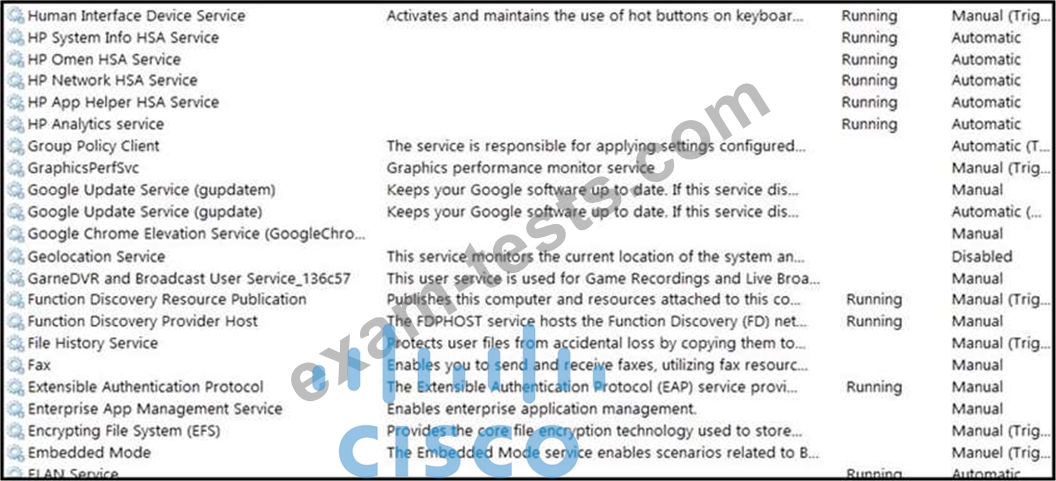
An engineer received multiple reports from employees unable to log into systems with the error: The Group Policy Client service failed to logon - Access is denied. Through further analysis, the engineer discovered several unexpected modifications to system settings. Which type of breach is occurring?

An engineer received multiple reports from employees unable to log into systems with the error: The Group Policy Client service failed to logon - Access is denied. Through further analysis, the engineer discovered several unexpected modifications to system settings. Which type of breach is occurring?
Question 48
An analyst is alerted for a malicious file hash. After analysis, the analyst determined that an internal workstation is communicating over port 80 with an external server and that the file hash is associated with Duqu malware. Which tactics, techniques, and procedures align with this analysis?
Question 49
A security architect is working in a processing center and must implement a DLP solution to detect and prevent any type of copy and paste attempts of sensitive data within unapproved applications and removable devices. Which technical architecture must be used?
Question 50
An engineer received an alert of a zero-day vulnerability affecting desktop phones through which an attacker sends a crafted packet to a device, resets the credentials, makes the device unavailable, and allows a default administrator account login. Which step should an engineer take after receiving this alert?

