Question 51
An engineer received multiple reports from users trying to access a company website and instead of landing on the website, they are redirected to a malicious website that asks them to fill in sensitive personal dat a. Which type of attack is occurring?
Question 52
An engineer is utilizing interactive behavior analysis to test malware in a sandbox environment to see how the malware performs when it is successfully executed. A location is secured to perform reverse engineering on a piece of malware. What is the next step the engineer should take to analyze this malware?
Question 53
Refer to the exhibit.
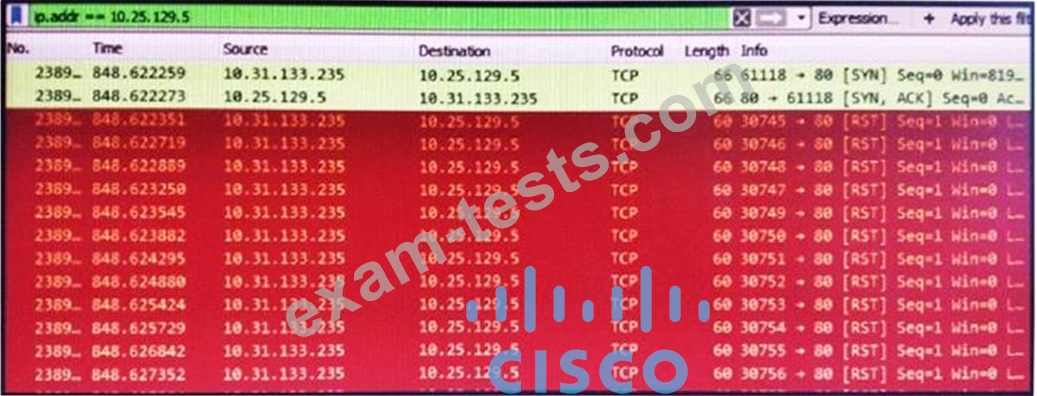
What is occurring in this packet capture?

What is occurring in this packet capture?
Question 54
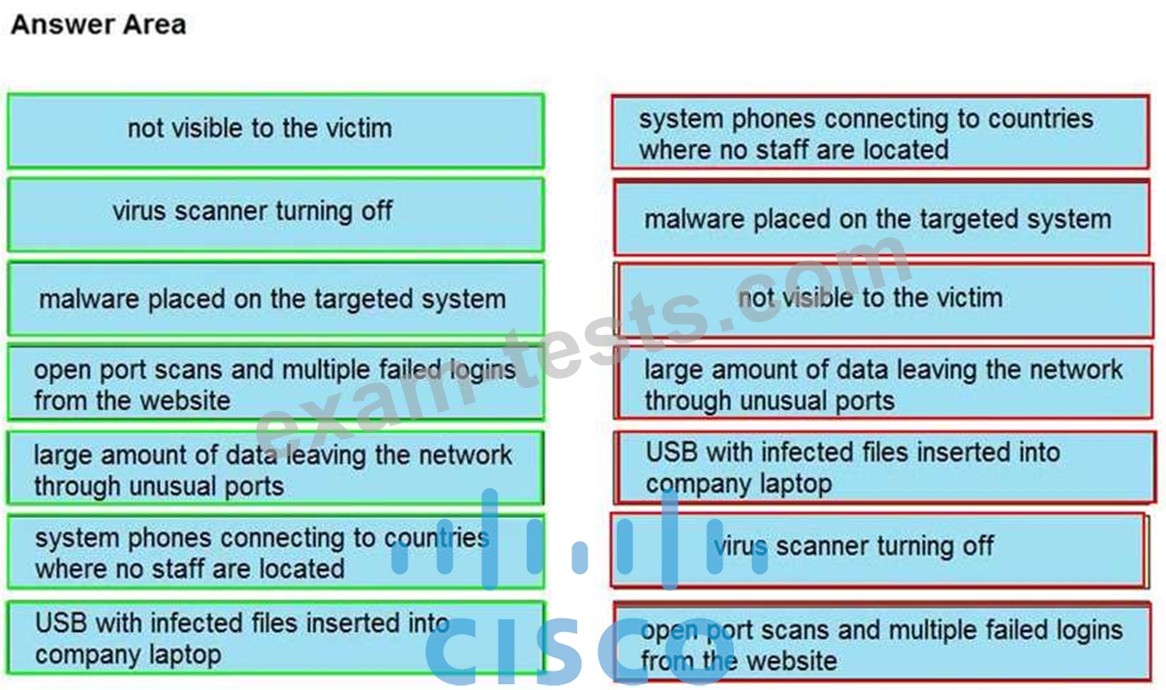
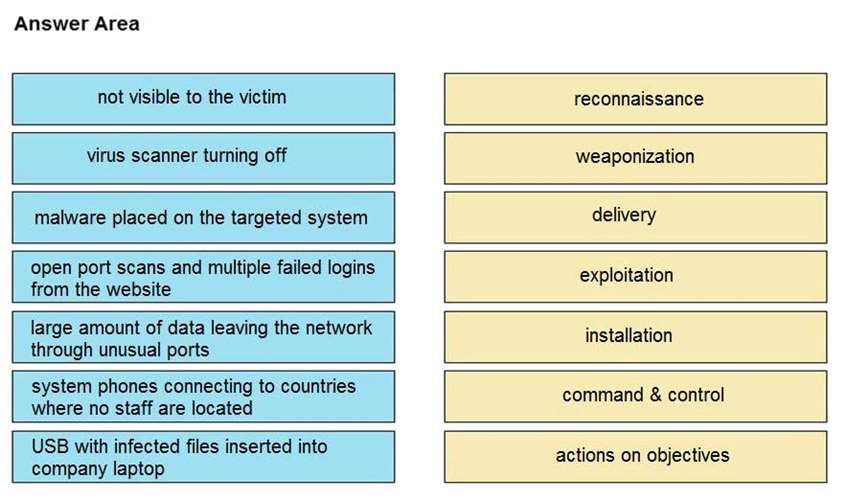
Drag and drop the type of attacks from the left onto the cyber kill chain stages at which the attacks are seen on the right.

Question 55
Refer to the exhibit.
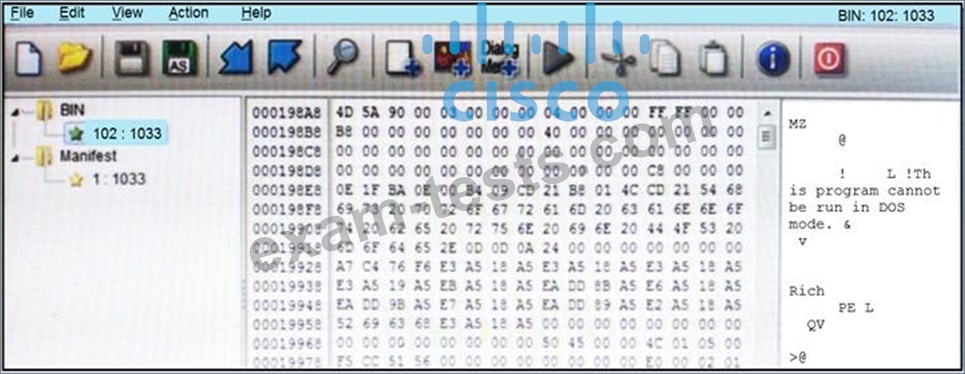
An engineer is reverse engineering a suspicious file by examining its resources. What does this file indicate?

An engineer is reverse engineering a suspicious file by examining its resources. What does this file indicate?