Question 56
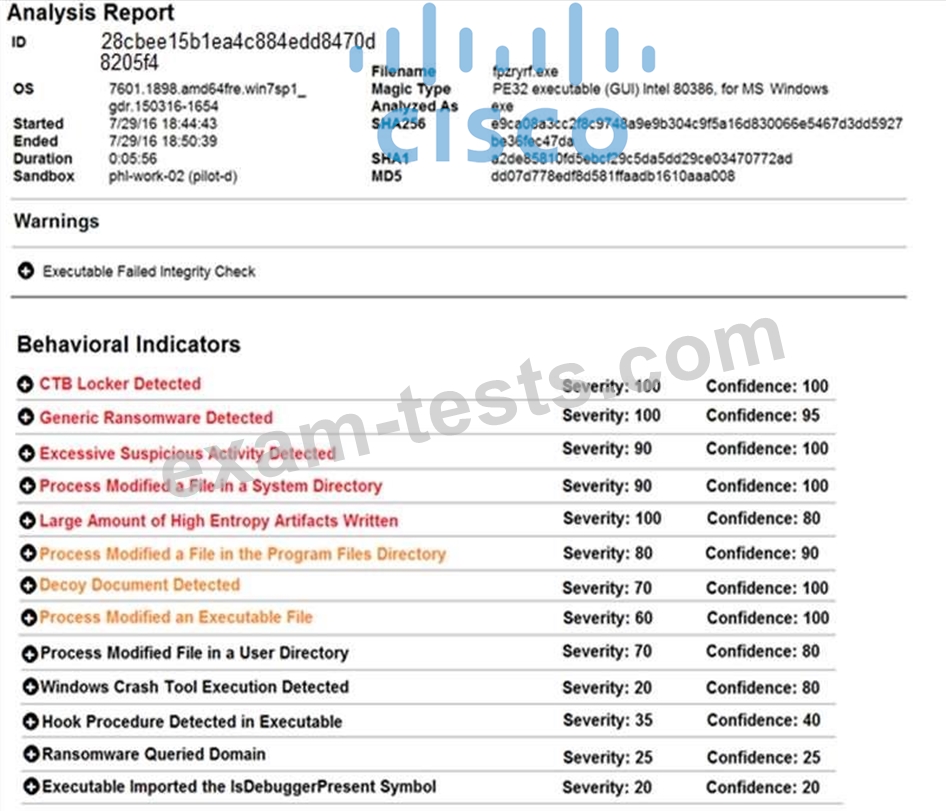
Refer to the exhibit. Cisco Advanced Malware Protection installed on an end-user desktop has automatically submitted a low prevalence file to the Threat Grid analysis engine for further analysis. What should be concluded from this report?
Question 57
Refer to the exhibit.
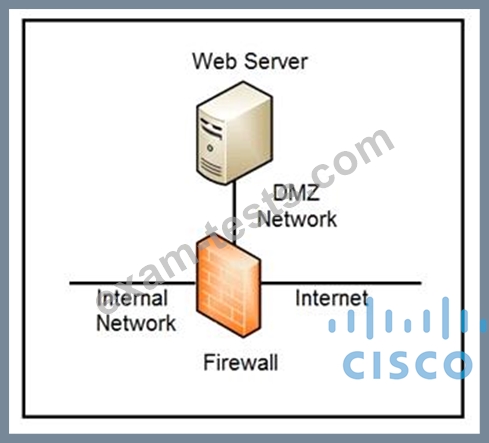
Which two steps mitigate attacks on the webserver from the Internet? (Choose two.)

Which two steps mitigate attacks on the webserver from the Internet? (Choose two.)
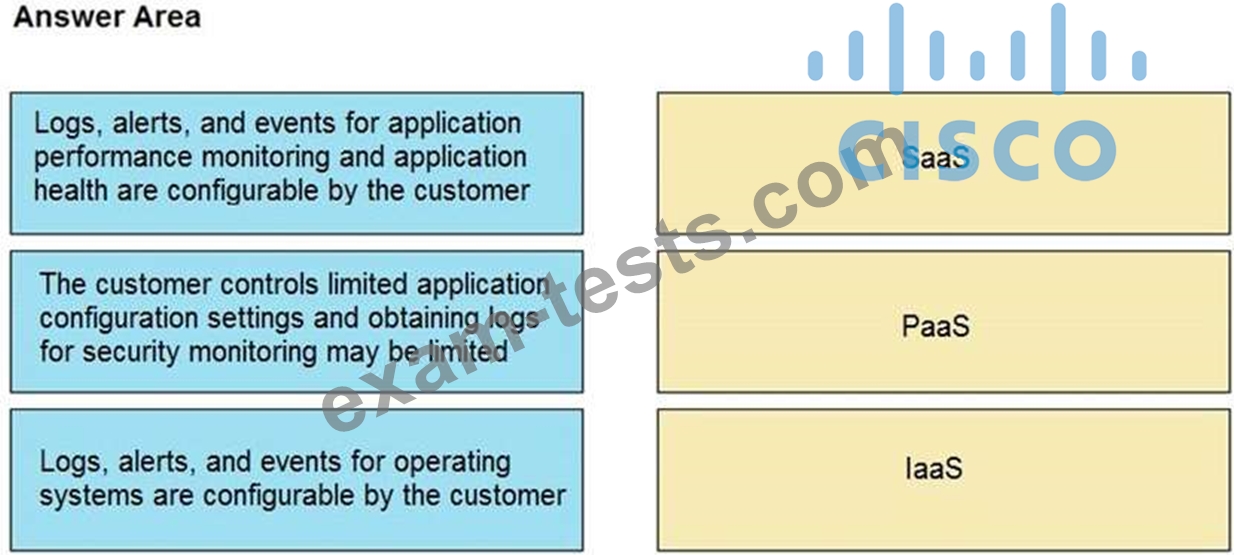
Question 58
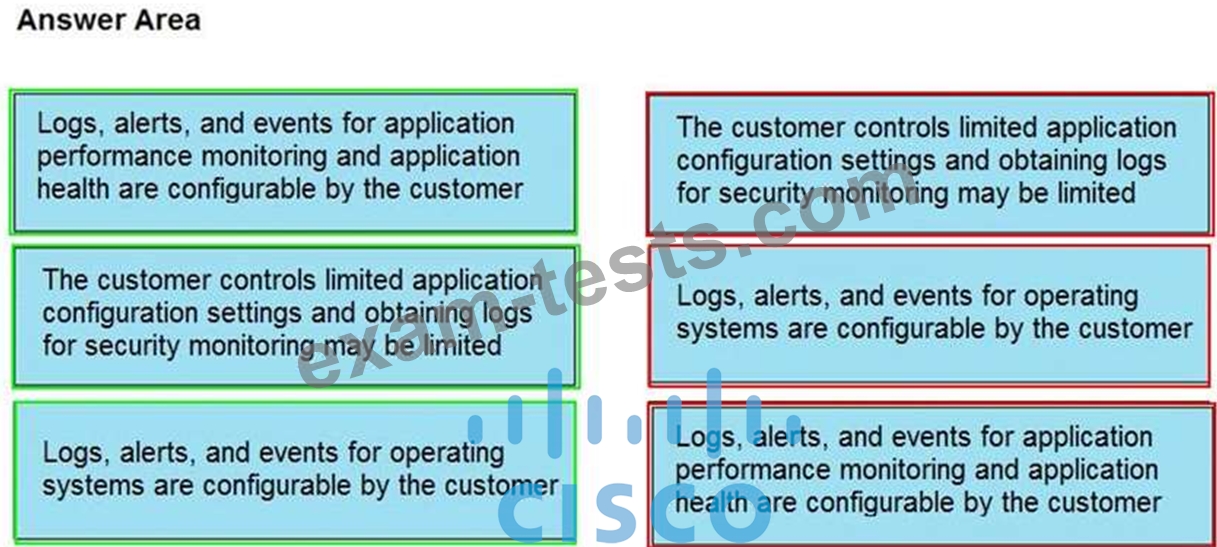
Drag and drop the telemetry-related considerations from the left onto their cloud service models on the right.

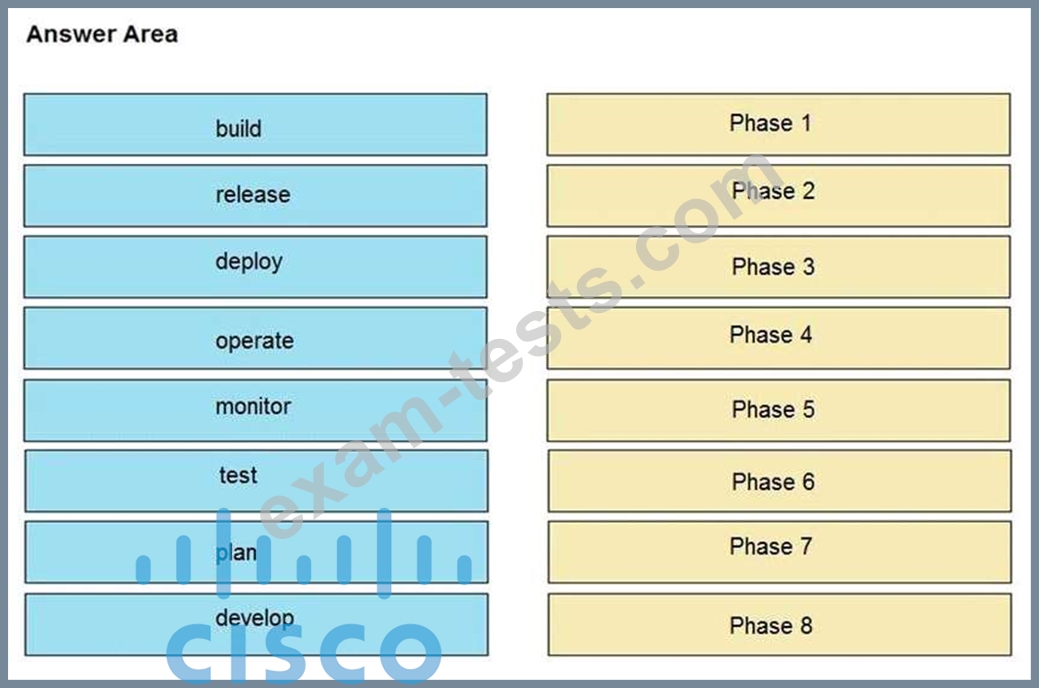
Question 59
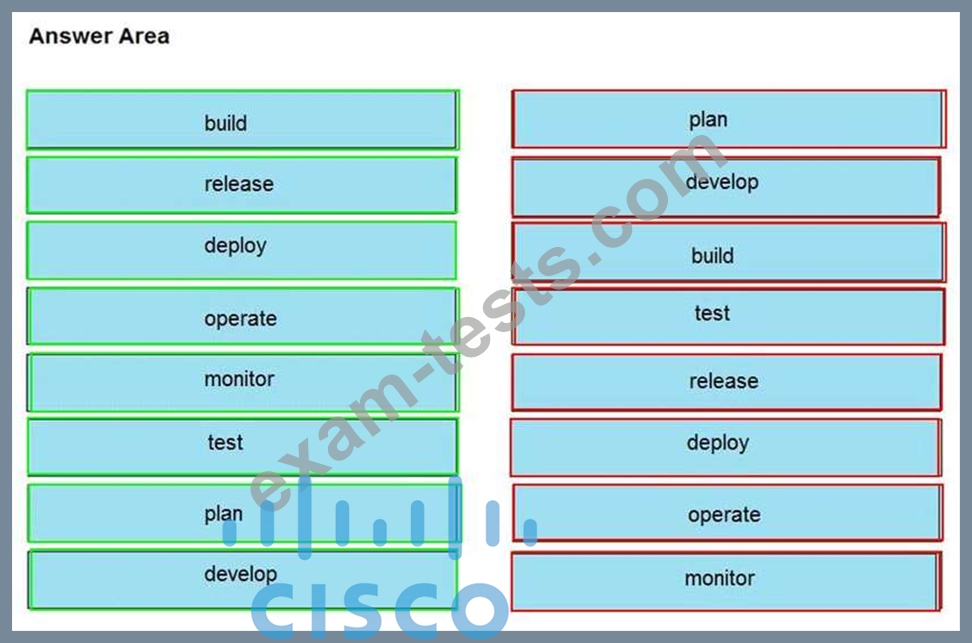
Drag and drop the components from the left onto the phases of the CI/CD pipeline on the right.

Question 60
A security manager received an email from an anomaly detection service, that one of their contractors has downloaded 50 documents from the company's confidential document management folder using a company- owned asset al039-ice-4ce687TL0500. A security manager reviewed the content of downloaded documents and noticed that the data affected is from different departments. What are the actions a security manager should take?