Question 51
Which flaw does an attacker leverage when exploiting SQL injection vulnerabilities?
Question 52
After a recent breach, an organization determined that phishing was used to gain initial access to the network before regaining persistence. The information gained from the phishing attack was a result of users visiting known malicious websites. What must be done in order to prevent this from happening in the future?
Question 53
Refer to the exhibit.
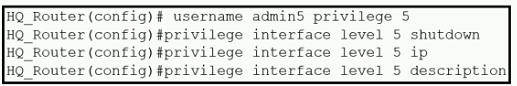
A network administrator configures command authorization for the admm5 user. What is the admin5 user able to do on HQ_Router after this configuration?

A network administrator configures command authorization for the admm5 user. What is the admin5 user able to do on HQ_Router after this configuration?
Question 54
Which two kinds of attacks are prevented by multifactor authentication? (Choose two.)
Question 55
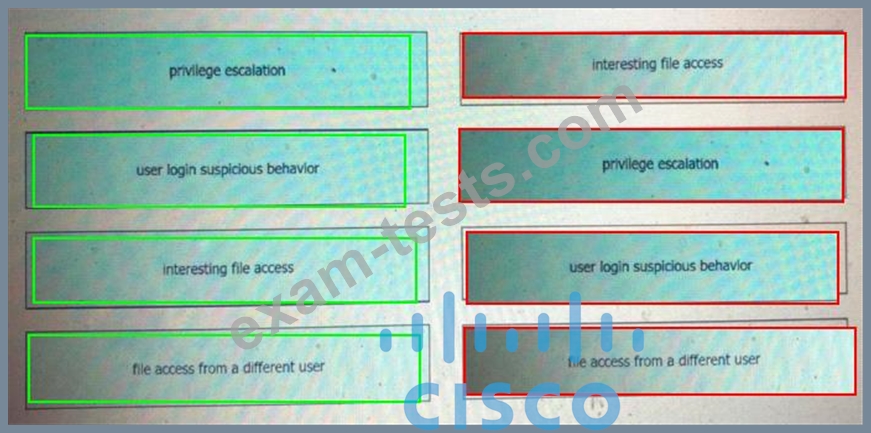
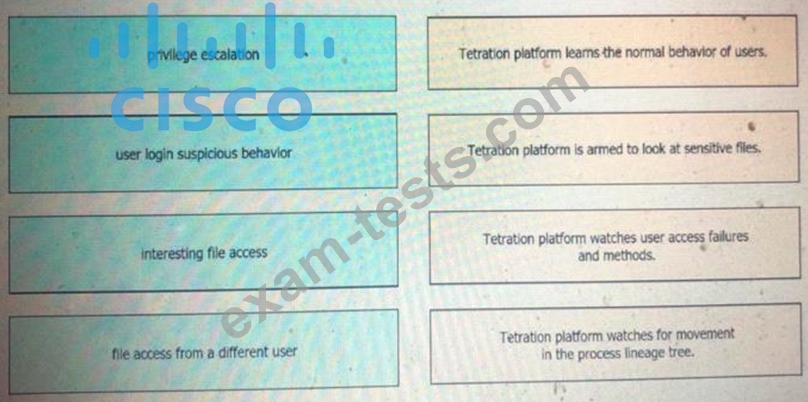
Drag and drop the suspicious patterns for the Cisco Tetration platform from the left onto the correct definitions on the right.

Premium Bundle
Newest 350-701 Exam PDF Dumps shared by BraindumpsPass.com for Helping Passing 350-701 Exam! BraindumpsPass.com now offer the updated 350-701 exam dumps, the BraindumpsPass.com 350-701 exam questions have been updated and answers have been corrected get the latest BraindumpsPass.com 350-701 pdf dumps with Exam Engine here: