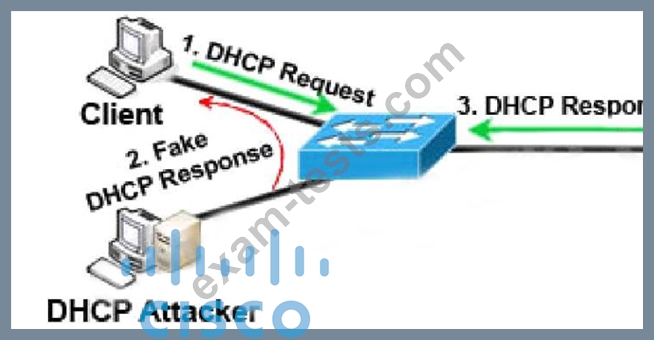
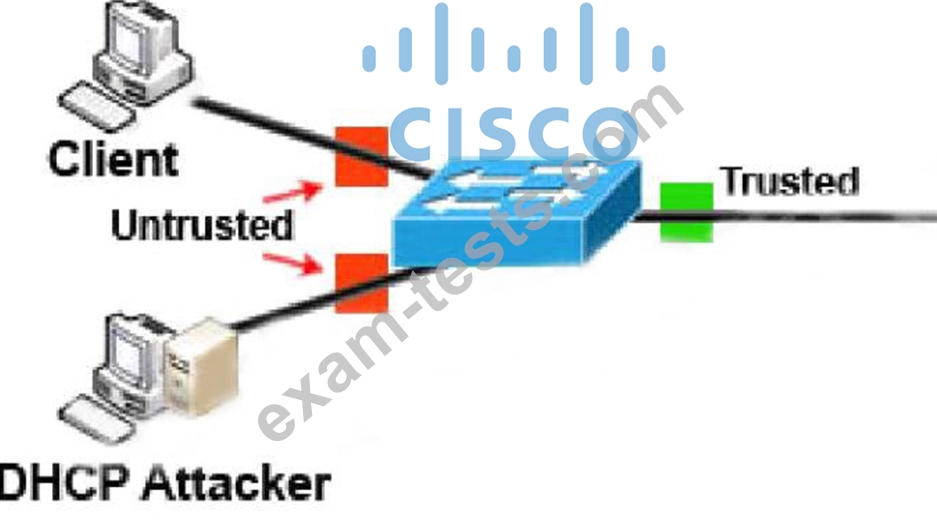
Question 56
An administrator is configuring a DHCP server to better secure their environment. They need to be able to ratelimit the traffic and ensure that legitimate requests are not dropped. How would this be accomplished?
Question 57
Which algorithm provides encryption and authentication for data plane communication?
Question 58
Which threat involves software being used to gain unauthorized access to a computer system?
Question 59
Which cloud model is a collaborative effort where infrastructure is shared and jointly accessed by several organizations from a specific group?
Question 60
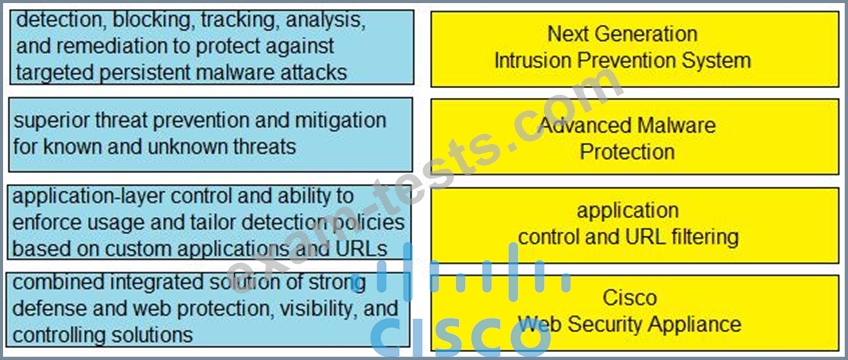
Drag and drop the capabilities from the left onto the correct technologies on the right.

Premium Bundle
Newest 350-701 Exam PDF Dumps shared by BraindumpsPass.com for Helping Passing 350-701 Exam! BraindumpsPass.com now offer the updated 350-701 exam dumps, the BraindumpsPass.com 350-701 exam questions have been updated and answers have been corrected get the latest BraindumpsPass.com 350-701 pdf dumps with Exam Engine here: