Question 36
Refer to the exhibit.
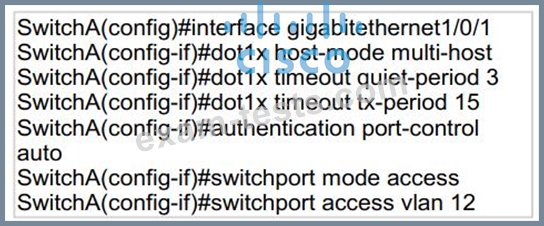
An engineer configured wired 802.1x on the network and is unable to get a laptop to authenticate. Which port configuration is missing?

An engineer configured wired 802.1x on the network and is unable to get a laptop to authenticate. Which port configuration is missing?
Question 37
An organization wants to secure data in a cloud environment Its security model requires that all users be authenticated and authorized Security configuration and posture must be continuously validated before access is granted or maintained to applications and data There is also a need to allow certain application traffic and deny all other traffic by default Which technology must be used to implement these requirements?
Question 38
Which proxy mode must be used on Cisco WSA to redirect TCP traffic with WCCP?
Question 39
Which Talos reputation center allows you to track the reputation of IP addresses for email and web traffic?
Question 40
Which protocol provides the strongest throughput performance when using Cisco AnyConnect VPN?

