Question 116
Using Cisco Firepower's Security Intelligence policies, upon which two criteria is Firepower block based? (Choose two.)
Question 117
Refer to the exhibit.
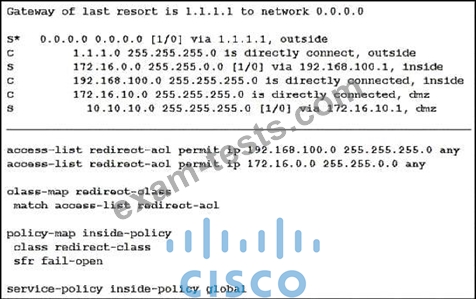
What is a result of the configuration?

What is a result of the configuration?
Question 118
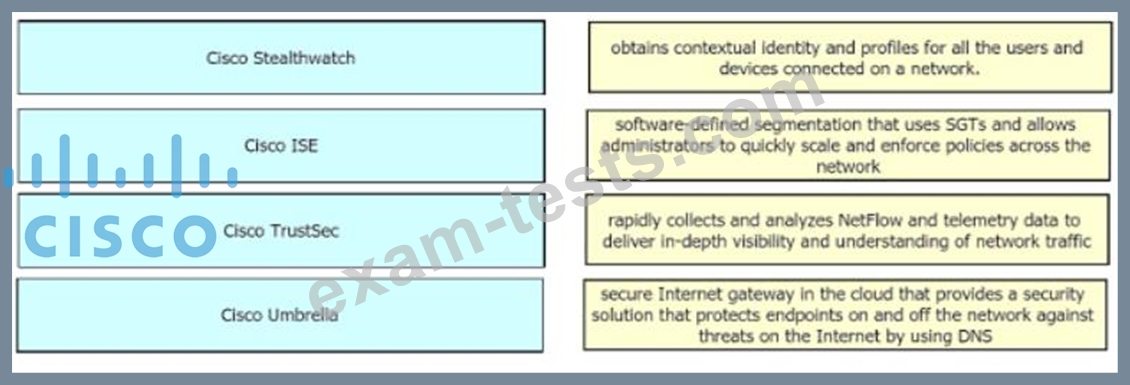
Drag and drop the solutions from the left onto the solution's benefits on the right.

Question 119
What is the purpose of CA in a PKI?
Question 120
An organization is receiving SPAM emails from a known malicious domain. What must be configured in order to prevent the session during the initial TCP communication?



