Question 56
An organization wants to secure data in a cloud environment. Its security model requires that all users be authenticated and authorized. Security configuration and posture must be continuously validated before access is granted or maintained to applications and dat a. There is also a need to allow certain application traffic and deny all other traffic by default. Which technology must be used to implement these requirements?
Question 57
Elliptic curve cryptography is a stronger more efficient cryptography method meant to replace which current encryption technology?
Question 58
Which group within Cisco writes and publishes a weekly newsletter to help cybersecurity professionals remain aware of the ongoing and most prevalent threats?
Question 59
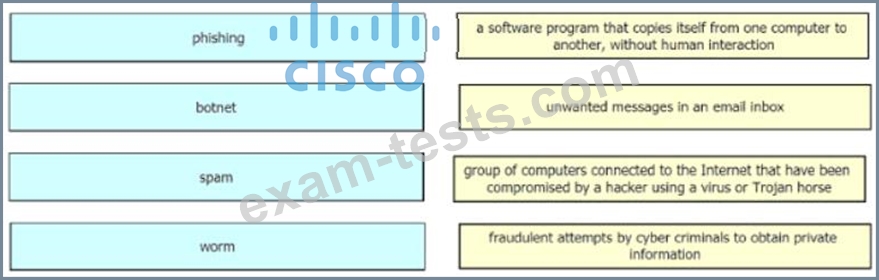
Drag and drop the common security threats from the left onto the definitions on the right.

Question 60
An organization is trying to improve their Defense in Depth by blocking malicious destinations prior to a connection being established. The solution must be able to block certain applications from being used within the network Which product should be used to accomplish this goal?



