Question 71
What are the two most commonly used authentication factors in multifactor authentication? (Choose two.)


Question 72
An organization is using Cisco Firepower and Cisco Meraki MX for network security and needs to centrally manage cloud policies across these platforms. Which software should be used to accomplish this goal?
Question 73
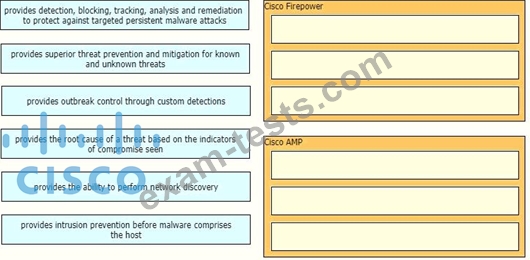
Drag and drop the capabilities of Cisco Firepower versus Cisco AMP from the left into the appropriate category on the right.

Question 74
A Cisco FTD engineer is creating a new IKEv2 policy called s2s00123456789 for their organization to allow for additional protocols to terminate network devices with. They currently only have one policy established and need the new policy to be a backup in case some devices cannot support the stronger algorithms listed in the primary policy. What should be done in order to support this?
Question 75
Refer to the exhibit.

Which command was used to display this output?

Which command was used to display this output?


