Question 61
What is the result of running the crypto isakmp key ciscXXXXXXXX address 172.16.0.0 command?.
Question 62
An organization wants to secure users, data, and applications in the cloud The solution must be API-based and operate as a cloud-native CAS8 Much solution must be used for this implementation?
Question 63
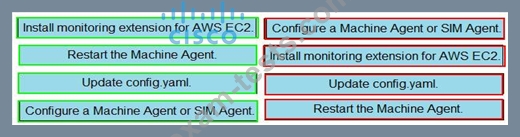
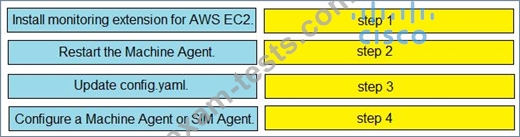
Drag and drop the steps from the left into the correct order on the right to enable AppDynamics to monitor an EC2 instance in Amazon Web Services.

Question 64
Elliptic curve cryptography is a stronger more efficient cryptography method meant to replace which current encryption technology?
Question 65
Which term describes when the Cisco Firepower downloads threat intelligence updates from Cisco Talos?