- Home
- Cisco Certification
- 350-701 Exam
- Cisco.350-701.v2022-10-19.q571 Practice Test
Question 386
An engineer wants to generate NetFlow records on traffic traversing the Cisco ASA.
Which Cisco ASA command must be used?
Which Cisco ASA command must be used?
Correct Answer: A
The syntax of this command is: flow-export destination interface-name ipv4-address | hostname udp-port This command is used on Cisco ASA to configure Network Secure Event Logging (NSEL) collector to which NetFlow packets are sent. The destination keyword indicates that a NSEL collector is being configured.
+ The interface-name argument is the name of the ASA and ASA Services Module interface through which the collector is reached.
+ The ipv4-address argument is the IP address of the machine running the collector application.
+ The hostname argument is the destination IP address or name of the collector.
+ The udp-port argument is the UDP port number to which NetFlow packets are sent.
You can configure a maximum of five collectors. After a collector is configured, template records are automatically sent to all configured NSEL collectors.
The syntax of this command is: flow-export destination interface-name ipv4-address | hostname udp-port This command is used on Cisco ASA to configure Network Secure Event Logging (NSEL) collector to which NetFlow packets are sent. The destination keyword indicates that a NSEL collector is being configured.
+ The interface-name argument is the name of the ASA and ASA Services Module interface through which the collector is reached.
+ The ipv4-address argument is the IP address of the machine running the collector application.
+ The hostname argument is the destination IP address or name of the collector.
+ The udp-port argument is the UDP port number to which NetFlow packets are sent.
You can configure a maximum of five collectors. After a collector is configured, template records are automatically sent to all configured NSEL collectors.
Reference:
monitor_nsel.html
The syntax of this command is: flow-export destination interface-name ipv4-address | hostname udp-port This command is used on Cisco ASA to configure Network Secure Event Logging (NSEL) collector to which NetFlow packets are sent. The destination keyword indicates that a NSEL collector is being configured.
+ The interface-name argument is the name of the ASA and ASA Services Module interface through which the collector is reached.
+ The ipv4-address argument is the IP address of the machine running the collector application.
+ The hostname argument is the destination IP address or name of the collector.
+ The udp-port argument is the UDP port number to which NetFlow packets are sent.
You can configure a maximum of five collectors. After a collector is configured, template records are automatically sent to all configured NSEL collectors.
monitor_nsel.html
+ The interface-name argument is the name of the ASA and ASA Services Module interface through which the collector is reached.
+ The ipv4-address argument is the IP address of the machine running the collector application.
+ The hostname argument is the destination IP address or name of the collector.
+ The udp-port argument is the UDP port number to which NetFlow packets are sent.
You can configure a maximum of five collectors. After a collector is configured, template records are automatically sent to all configured NSEL collectors.
The syntax of this command is: flow-export destination interface-name ipv4-address | hostname udp-port This command is used on Cisco ASA to configure Network Secure Event Logging (NSEL) collector to which NetFlow packets are sent. The destination keyword indicates that a NSEL collector is being configured.
+ The interface-name argument is the name of the ASA and ASA Services Module interface through which the collector is reached.
+ The ipv4-address argument is the IP address of the machine running the collector application.
+ The hostname argument is the destination IP address or name of the collector.
+ The udp-port argument is the UDP port number to which NetFlow packets are sent.
You can configure a maximum of five collectors. After a collector is configured, template records are automatically sent to all configured NSEL collectors.
Reference:
monitor_nsel.html
The syntax of this command is: flow-export destination interface-name ipv4-address | hostname udp-port This command is used on Cisco ASA to configure Network Secure Event Logging (NSEL) collector to which NetFlow packets are sent. The destination keyword indicates that a NSEL collector is being configured.
+ The interface-name argument is the name of the ASA and ASA Services Module interface through which the collector is reached.
+ The ipv4-address argument is the IP address of the machine running the collector application.
+ The hostname argument is the destination IP address or name of the collector.
+ The udp-port argument is the UDP port number to which NetFlow packets are sent.
You can configure a maximum of five collectors. After a collector is configured, template records are automatically sent to all configured NSEL collectors.
monitor_nsel.html
Question 387
What are two Detection and Analytics Engines of Cognitive Threat Analytics? (Choose two)
Correct Answer: A,B
Explanation Cisco Cognitive Threat Analytics helps you quickly detect and respond to sophisticated, clandestine attacks that are already under way or are attempting to establish a presence within your environment. The solution automatically identifies and investigates suspicious or malicious web-based traffic. It identifies both potential and confirmed threats, allowing you to quickly remediate the infection and reduce the scope and damage of an attack, whether it's a known threat campaign that has spread across multiple organizations or a unique threat you've never seen before. Detection and analytics features provided in Cognitive Threat Analytics are shown below: + Data exfiltration: Cognitive Threat Analytics uses statistical modeling of an organization's network to identify anomalous web traffic and pinpoint the exfiltration of sensitive data. It recognizes data exfiltration even in HTTPS-encoded traffic, without any need for you to decrypt transferred content + Command-and-control (C2) communication: Cognitive Threat Analytics combines a wide range of data, ranging from statistics collected on an Internet-wide level to host-specific local anomaly scores. Combining these indicators inside the statistical detection algorithms allows us to distinguish C2 communication from benign traffic and from other malicious activities. Cognitive Threat Analytics recognizes C2 even in HTTPSencoded or anonymous traffic, including Tor, without any need to decrypt transferred content, detecting a broad range of threats ... Reference: https://www.cisco.com/c/dam/en/us/products/collateral/security/cognitive-threat-analytics/at-aglance-c45-736555.pdf Cisco Cognitive Threat Analytics helps you quickly detect and respond to sophisticated, clandestine attacks that are already under way or are attempting to establish a presence within your environment. The solution automatically identifies and investigates suspicious or malicious web-based traffic. It identifies both potential and confirmed threats, allowing you to quickly remediate the infection and reduce the scope and damage of an attack, whether it's a known threat campaign that has spread across multiple organizations or a unique threat you've never seen before.
Detection and analytics features provided in Cognitive Threat Analytics are shown below:
+ Data exfiltration: Cognitive Threat Analytics uses statistical modeling of an organization's network to identify anomalous web traffic and pinpoint the exfiltration of sensitive data. It recognizes data exfiltration even in HTTPS-encoded traffic, without any need for you to decrypt transferred content
+ Command-and-control (C2) communication: Cognitive Threat Analytics combines a wide range of data, ranging from statistics collected on an Internet-wide level to host-specific local anomaly scores. Combining these indicators inside the statistical detection algorithms allows us to distinguish C2 communication from benign traffic and from other malicious activities. Cognitive Threat Analytics recognizes C2 even in HTTPSencoded or anonymous traffic, including Tor, without any need to decrypt transferred content, detecting a broad range of threats
...
Explanation Cisco Cognitive Threat Analytics helps you quickly detect and respond to sophisticated, clandestine attacks that are already under way or are attempting to establish a presence within your environment. The solution automatically identifies and investigates suspicious or malicious web-based traffic. It identifies both potential and confirmed threats, allowing you to quickly remediate the infection and reduce the scope and damage of an attack, whether it's a known threat campaign that has spread across multiple organizations or a unique threat you've never seen before. Detection and analytics features provided in Cognitive Threat Analytics are shown below: + Data exfiltration: Cognitive Threat Analytics uses statistical modeling of an organization's network to identify anomalous web traffic and pinpoint the exfiltration of sensitive data. It recognizes data exfiltration even in HTTPS-encoded traffic, without any need for you to decrypt transferred content + Command-and-control (C2) communication: Cognitive Threat Analytics combines a wide range of data, ranging from statistics collected on an Internet-wide level to host-specific local anomaly scores. Combining these indicators inside the statistical detection algorithms allows us to distinguish C2 communication from benign traffic and from other malicious activities. Cognitive Threat Analytics recognizes C2 even in HTTPSencoded or anonymous traffic, including Tor, without any need to decrypt transferred content, detecting a broad range of threats ... Reference: https://www.cisco.com/c/dam/en/us/products/collateral/security/cognitive-threat-analytics/at-aglance-c45-736555.pdf
Detection and analytics features provided in Cognitive Threat Analytics are shown below:
+ Data exfiltration: Cognitive Threat Analytics uses statistical modeling of an organization's network to identify anomalous web traffic and pinpoint the exfiltration of sensitive data. It recognizes data exfiltration even in HTTPS-encoded traffic, without any need for you to decrypt transferred content
+ Command-and-control (C2) communication: Cognitive Threat Analytics combines a wide range of data, ranging from statistics collected on an Internet-wide level to host-specific local anomaly scores. Combining these indicators inside the statistical detection algorithms allows us to distinguish C2 communication from benign traffic and from other malicious activities. Cognitive Threat Analytics recognizes C2 even in HTTPSencoded or anonymous traffic, including Tor, without any need to decrypt transferred content, detecting a broad range of threats
...
Explanation Cisco Cognitive Threat Analytics helps you quickly detect and respond to sophisticated, clandestine attacks that are already under way or are attempting to establish a presence within your environment. The solution automatically identifies and investigates suspicious or malicious web-based traffic. It identifies both potential and confirmed threats, allowing you to quickly remediate the infection and reduce the scope and damage of an attack, whether it's a known threat campaign that has spread across multiple organizations or a unique threat you've never seen before. Detection and analytics features provided in Cognitive Threat Analytics are shown below: + Data exfiltration: Cognitive Threat Analytics uses statistical modeling of an organization's network to identify anomalous web traffic and pinpoint the exfiltration of sensitive data. It recognizes data exfiltration even in HTTPS-encoded traffic, without any need for you to decrypt transferred content + Command-and-control (C2) communication: Cognitive Threat Analytics combines a wide range of data, ranging from statistics collected on an Internet-wide level to host-specific local anomaly scores. Combining these indicators inside the statistical detection algorithms allows us to distinguish C2 communication from benign traffic and from other malicious activities. Cognitive Threat Analytics recognizes C2 even in HTTPSencoded or anonymous traffic, including Tor, without any need to decrypt transferred content, detecting a broad range of threats ... Reference: https://www.cisco.com/c/dam/en/us/products/collateral/security/cognitive-threat-analytics/at-aglance-c45-736555.pdf
Question 388
Refer to the exhibit.
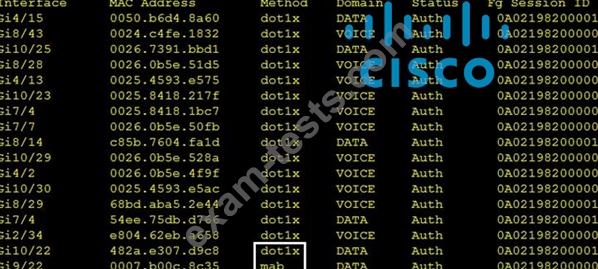
Which command was used to generate this output and to show which ports are authenticating with dot1x or mab?

Which command was used to generate this output and to show which ports are authenticating with dot1x or mab?
Correct Answer: D
Question 389
An engineer used a posture check on a Microsoft Windows endpoint and discovered that the MS17-010 patch was not installed, which left the endpoint vulnerable to WannaCry ransomware. Which two solutions mitigate the risk of this ransomware infection? (Choose two.)
Correct Answer: A,B
Question 390
How is DNS tunneling used to exfiltrate data out of a corporate network?
Correct Answer: B
Explanation
Domain name system (DNS) is the protocol that translates human-friendly URLs, such as securitytut.com, into IP addresses, such as 183.33.24.13. Because DNS messages are only used as the beginning of each communication and they are not intended for data transfer, many organizations do not monitor their DNS traffic for malicious activity. As a result, DNS-based attacks can be effective if launched against their networks. DNS tunneling is one such attack.
An example of DNS Tunneling is shown below:

The attacker incorporates one of many open-source DNS tunneling kits into an authoritative DNS nameserver (NS) and malicious payload.
2. An IP address (e.g. 1.2.3.4) is allocated from the attacker's infrastructure and a domain name (e.g. attackerdomain.com) is registered or reused. The registrar informs the top-level domain (.com) nameservers to refer requests for attackerdomain.com to ns.attackerdomain.com, which has a DNS record mapped to 1.2.3.4
3. The attacker compromises a system with the malicious payload. Once the desired data is obtained, the payload encodes the data as a series of 32 characters (0-9, A-Z) broken into short strings (3KJ242AIE9, P028X977W,...).
4. The payload initiates thousands of unique DNS record requests to the attacker's domain with each string as a part of the domain name (e.g. 3KJ242AIE9.attackerdomain.com). Depending on the attacker's patience and stealth, requests can be spaced out over days or months to avoid suspicious network activity. 5. The requests are forwarded to a recursive DNS resolver. During resolution, the requests are sent to the attacker's authoritative DNS nameserver, 6. The tunneling kit parses the encoded strings and rebuilds the exfiltrated data. Reference: https://learn-umbrella.cisco.com/i/775902-dns-tunneling/0
5. The requests are forwarded to a recursive DNS resolver. During resolution, the requests are sent to the attacker's authoritative DNS nameserver,
6. The tunneling kit parses the encoded strings and rebuilds the exfiltrated data.
a part of the domain name (e.g. 3KJ242AIE9.attackerdomain.com). Depending on the attacker's patience and stealth, requests can be spaced out over days or months to avoid suspicious network activity. 5. The requests are forwarded to a recursive DNS resolver. During resolution, the requests are sent to the attacker's authoritative DNS nameserver, 6. The tunneling kit parses the encoded strings and rebuilds the exfiltrated data. Reference: https://learn-umbrella.cisco.com/i/775902-dns-tunneling/0
Domain name system (DNS) is the protocol that translates human-friendly URLs, such as securitytut.com, into IP addresses, such as 183.33.24.13. Because DNS messages are only used as the beginning of each communication and they are not intended for data transfer, many organizations do not monitor their DNS traffic for malicious activity. As a result, DNS-based attacks can be effective if launched against their networks. DNS tunneling is one such attack.
An example of DNS Tunneling is shown below:

The attacker incorporates one of many open-source DNS tunneling kits into an authoritative DNS nameserver (NS) and malicious payload.
2. An IP address (e.g. 1.2.3.4) is allocated from the attacker's infrastructure and a domain name (e.g. attackerdomain.com) is registered or reused. The registrar informs the top-level domain (.com) nameservers to refer requests for attackerdomain.com to ns.attackerdomain.com, which has a DNS record mapped to 1.2.3.4
3. The attacker compromises a system with the malicious payload. Once the desired data is obtained, the payload encodes the data as a series of 32 characters (0-9, A-Z) broken into short strings (3KJ242AIE9, P028X977W,...).
4. The payload initiates thousands of unique DNS record requests to the attacker's domain with each string as a part of the domain name (e.g. 3KJ242AIE9.attackerdomain.com). Depending on the attacker's patience and stealth, requests can be spaced out over days or months to avoid suspicious network activity. 5. The requests are forwarded to a recursive DNS resolver. During resolution, the requests are sent to the attacker's authoritative DNS nameserver, 6. The tunneling kit parses the encoded strings and rebuilds the exfiltrated data. Reference: https://learn-umbrella.cisco.com/i/775902-dns-tunneling/0
5. The requests are forwarded to a recursive DNS resolver. During resolution, the requests are sent to the attacker's authoritative DNS nameserver,
6. The tunneling kit parses the encoded strings and rebuilds the exfiltrated data.
a part of the domain name (e.g. 3KJ242AIE9.attackerdomain.com). Depending on the attacker's patience and stealth, requests can be spaced out over days or months to avoid suspicious network activity. 5. The requests are forwarded to a recursive DNS resolver. During resolution, the requests are sent to the attacker's authoritative DNS nameserver, 6. The tunneling kit parses the encoded strings and rebuilds the exfiltrated data. Reference: https://learn-umbrella.cisco.com/i/775902-dns-tunneling/0
- Other Version
- 1537Cisco.350-701.v2025-10-04.q562
- 1078Cisco.350-701.v2025-06-19.q238
- 1568Cisco.350-701.v2024-12-18.q472
- 2735Cisco.350-701.v2023-08-01.q405
- 3451Cisco.350-701.v2023-05-04.q372
- 2368Cisco.350-701.v2023-03-16.q218
- 7278Cisco.350-701.v2022-07-08.q453
- 4202Cisco.350-701.v2022-02-02.q204
- 116Cisco.Prepawaypdf.350-701.v2021-12-15.by.ellen.316q.pdf
- Latest Upload
- 115EC-COUNCIL.312-76.v2026-01-03.q103
- 116PaloAltoNetworks.PSE-Cortex-Pro-24.v2026-01-03.q62
- 107MedicalTests.AAPC-CPC.v2026-01-03.q50
- 114SAP.C_S4CPB_2502.v2026-01-03.q43
- 129USGBC.LEED-AP-Homes.v2026-01-02.q36
- 115SAP.C-THR94-2505.v2026-01-02.q29
- 137MedicalProfessional.CHFM.v2026-01-01.q37
- 116SAP.C-BCSPM-2502.v2026-01-01.q9
- 118Microsoft.MB-335.v2026-01-01.q142
- 124SAP.C_THR70_2505.v2026-01-01.q55
[×]
Download PDF File
Enter your email address to download Cisco.350-701.v2022-10-19.q571 Practice Test

