Question 396
An organization has two systems in their DMZ that have an unencrypted link between them for communication.
The organization does not have a defined password policy and uses several default accounts on the systems.
The application used on those systems also have not gone through stringent code reviews. Which vulnerability would help an attacker brute force their way into the systems?
The organization does not have a defined password policy and uses several default accounts on the systems.
The application used on those systems also have not gone through stringent code reviews. Which vulnerability would help an attacker brute force their way into the systems?
Question 397
Refer to the exhibit.
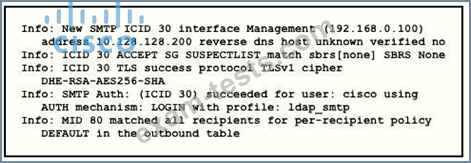
Which type of authentication is in use?

Which type of authentication is in use?
Question 398
What is the benefit of installing Cisco AMP for Endpoints on a network?
Question 399
An engineer is configuring a Cisco ESA and wants to control whether to accept or reject email messages to a recipient address.
Which list contains the allowed recipient addresses?
Which list contains the allowed recipient addresses?
Question 400
In which cloud services model is the tenant responsible for virtual machine OS patching?

