Question 56
You are a security analyst tasked with interpreting an Nmap scan output from Company A's privileged network.
The company's hardening guidelines indicate the following:
* There should be one primary server or service per device.
* Only default ports should be used.
* Non-secure protocols should be disabled.
INSTRUCTIONS
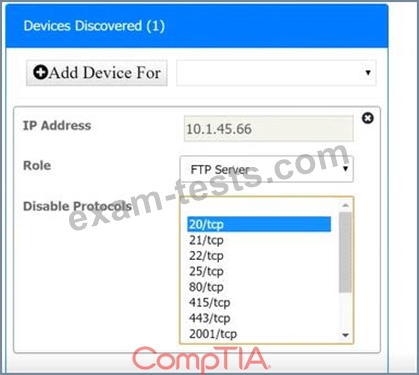
Using the Nmap output, identify the devices on the network and their roles, and any open ports that should be closed. For each device found, add a device entry to the Devices Discovered list, with the following information:
* The IP address of the device
* The primary server or service of the device
* The protocol(s) that should be disabled based on the hardening guidelines
The company's hardening guidelines indicate the following:
* There should be one primary server or service per device.
* Only default ports should be used.
* Non-secure protocols should be disabled.
INSTRUCTIONS
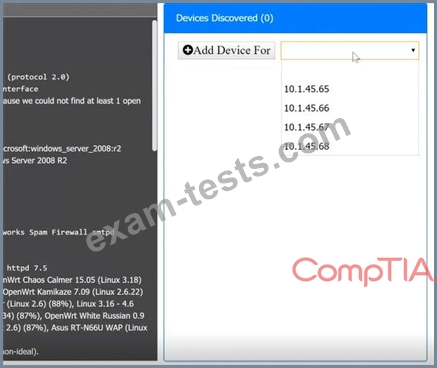
Using the Nmap output, identify the devices on the network and their roles, and any open ports that should be closed. For each device found, add a device entry to the Devices Discovered list, with the following information:
* The IP address of the device
* The primary server or service of the device
* The protocol(s) that should be disabled based on the hardening guidelines

Question 57
A security manager recently categorized an information system. During the categorization effort, the manager determined the loss of integrity of a specific information type would impact business significantly. Based on this, the security manager recommends the implementation of several solutions. Which of the following, when combined, would BEST mitigate this risk? (Choose two.)
Question 58
A company has gone through a round of phishing attacks. More than 200 users have had their workstation infected because they clicked on a link in an email. An incident analysis has determined an executable ran and compromised the administrator account on each workstation. Management is demanding the information security team prevent this from happening again.
Which of the following would BEST prevent this from happening again?
Which of the following would BEST prevent this from happening again?
Question 59
An organization has recently deployed an EDR solution across its laptops, desktops, and server infrastructure.
The organization's server infrastructure is deployed in an IaaS environment. A database within the non- production environment has been misconfigured with a routable IP and is communicating with a command and control server.
Which of the following procedures should the security responder apply to the situation? (Choose two.)
The organization's server infrastructure is deployed in an IaaS environment. A database within the non- production environment has been misconfigured with a routable IP and is communicating with a command and control server.
Which of the following procedures should the security responder apply to the situation? (Choose two.)
Question 60
A company monitors the performance of all web servers using WMI. A network administrator informs the security engineer that web servers hosting the company's client-facing portal are running slowly today. After some investigation, the security engineer notices a large number of attempts at enumerating host information via SNMP from multiple IP addresses.
Which of the following would be the BEST technique for the security engineer to employ in an attempt to prevent reconnaissance activity?
Which of the following would be the BEST technique for the security engineer to employ in an attempt to prevent reconnaissance activity?