Question 61
A company has hired an external security consultant to conduct a thorough review of all aspects of corporate security. The company is particularly concerned about unauthorized access to its physical offices resulting in network compromises. Which of the following should the consultant recommend be performed to evaluate potential risks?
Question 62
A security consultant is attempting to discover if the company is utilizing databases on client machines to store the customer data. The consultant reviews the following information:
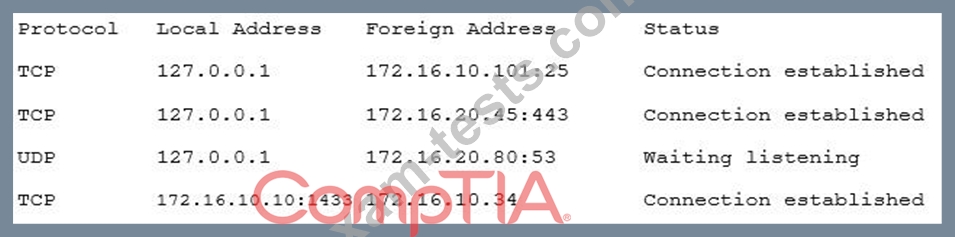
Which of the following commands would have providedthis output?

Which of the following commands would have providedthis output?
Question 63
A legacy web application, which is being used by a hospital, cannot be upgraded for 12 months. A new vulnerability is found in the legacy application, and the networking team is tasked with mitigation. Middleware for mitigation will cost $100,000 per year. Which of the following must be calculated to determine ROI?
(Choose two.)
(Choose two.)
Question 64
Given the following code snippet:
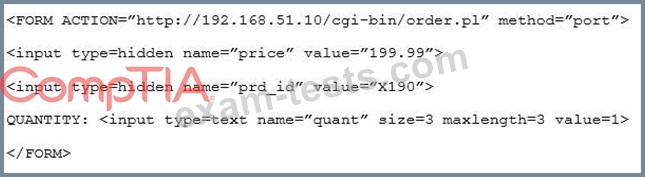
Of which of the following is this snippet an example?

Of which of the following is this snippet an example?
Question 65
A systems administrator at a medical imaging company discovers protected health information (PHI) on a general purpose file server. Which of the following steps should the administrator take NEXT?

