Question 46
A network administrator with a company's NSP has received a CERT alert for targeted adversarial behavior at the company. In addition to the company's physical security, which of the following can the network administrator use to detect the presence of a malicious actor physically accessing the company's network or information systems from within? (Select TWO).
Question 47
An organization is reviewing endpoint security solutions. In evaluating products, the organization has the following requirements:
1. Support server, laptop, and desktop infrastructure
2. Due to limited security resources, implement active protection capabilities
3. Provide users with the ability to self-service classify information and apply policies
4. Protect data-at-rest and data-in-use
Which of the following endpoint capabilities would BEST meet the above requirements? (Choose two.)
1. Support server, laptop, and desktop infrastructure
2. Due to limited security resources, implement active protection capabilities
3. Provide users with the ability to self-service classify information and apply policies
4. Protect data-at-rest and data-in-use
Which of the following endpoint capabilities would BEST meet the above requirements? (Choose two.)
Question 48
During the deployment of a new system, the implementation team determines that APIs used to integrate the new system with a legacy system are not functioning properly Further investigation shows there is a misconfigured encryption algorithm used to secure data transfers between systems.
Which of the following should the project manager use to determine the source of the defined algorithm in use?
Which of the following should the project manager use to determine the source of the defined algorithm in use?
Question 49
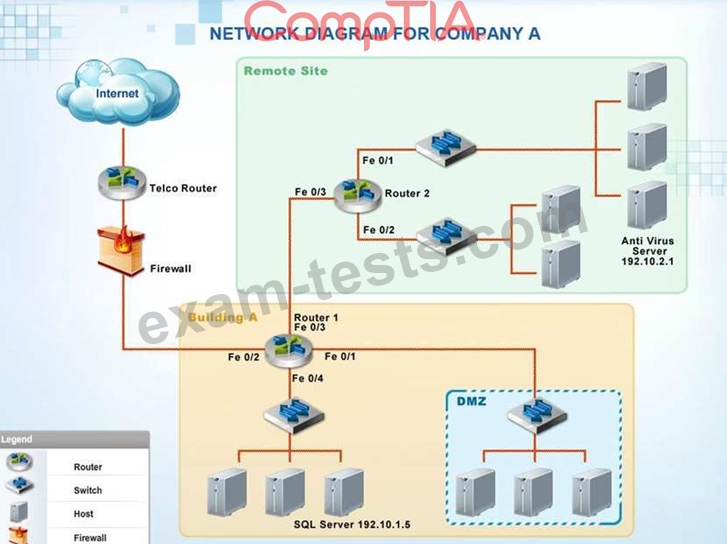
Company A has noticed abnormal behavior targeting their SQL server on the network from a rogue IP address.
The company uses the following internal IP address ranges: 192.10.1.0/24 for the corporate site and
192.10.2.0/24 for the remote site. The Telco router interface uses the 192.10.5.0/30 IP range.
Instructions: Click on the simulation button to refer to the Network Diagram for Company A.
Click on Router 1, Router 2, and the Firewall to evaluate and configure each device.
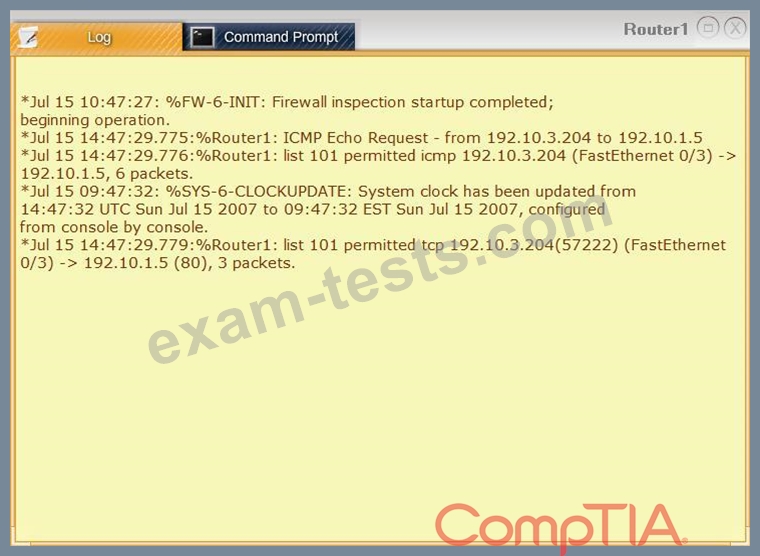
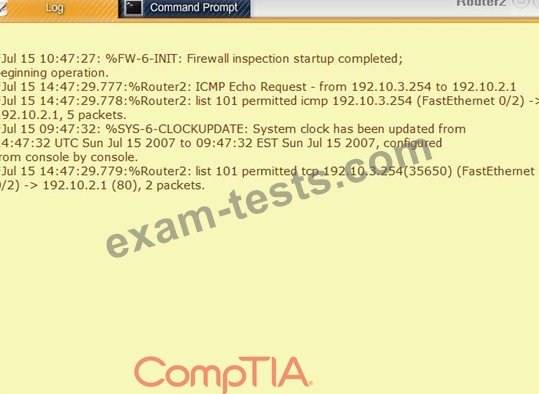
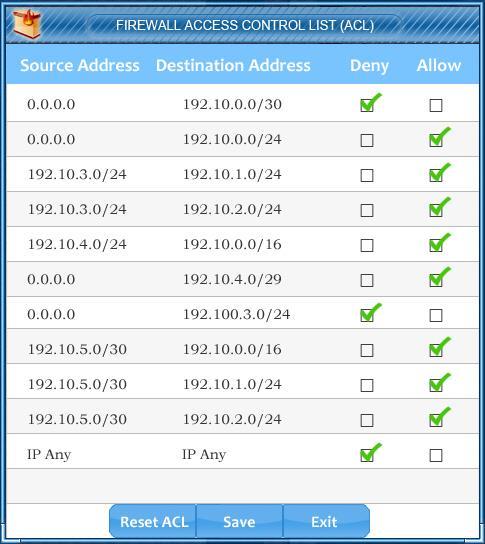
Task 1: Display and examine the logs and status of Router 1, Router 2, and Firewall interfaces.
Task 2: Reconfigure the appropriate devices to prevent the attacks from continuing to target the SQL server and other servers on the corporate network.
The company uses the following internal IP address ranges: 192.10.1.0/24 for the corporate site and
192.10.2.0/24 for the remote site. The Telco router interface uses the 192.10.5.0/30 IP range.
Instructions: Click on the simulation button to refer to the Network Diagram for Company A.
Click on Router 1, Router 2, and the Firewall to evaluate and configure each device.
Task 1: Display and examine the logs and status of Router 1, Router 2, and Firewall interfaces.
Task 2: Reconfigure the appropriate devices to prevent the attacks from continuing to target the SQL server and other servers on the corporate network.




Question 50
An engineer needs to provide access to company resources for several offshore contractors. The contractors require:
* Access to a number of applications, including internal websites
* Access to database data and the ability to manipulate it
* The ability to log into Linux and Windows servers remotely
Which of the following remote access technologies are the BEST choices to provide all of this access securely? (Choose two.)
* Access to a number of applications, including internal websites
* Access to database data and the ability to manipulate it
* The ability to log into Linux and Windows servers remotely
Which of the following remote access technologies are the BEST choices to provide all of this access securely? (Choose two.)
Premium Bundle
Newest CAS-003 Exam PDF Dumps shared by BraindumpsPass.com for Helping Passing CAS-003 Exam! BraindumpsPass.com now offer the updated CAS-003 exam dumps, the BraindumpsPass.com CAS-003 exam questions have been updated and answers have been corrected get the latest BraindumpsPass.com CAS-003 pdf dumps with Exam Engine here:

