Question 181
A developer has executed code for a website that allows users to search for employees' phone numbers by last name. The query string sent by the browser is as follows:
http://www.companywebsite.com/search.php?q=SMITH
The developer has implemented a well-known JavaScript sanitization library and stored procedures, but a penetration test shows the website is vulnerable to XSS. Which of the following should the developer implement NEXT to prevent XSS? (Choose two.)
http://www.companywebsite.com/search.php?q=SMITH
The developer has implemented a well-known JavaScript sanitization library and stored procedures, but a penetration test shows the website is vulnerable to XSS. Which of the following should the developer implement NEXT to prevent XSS? (Choose two.)
Question 182
A medical device company is implementing a new COTS antivirus solution in its manufacturing plant. All validated machines and instruments must be retested for interoperability with the new software. Which of the following would BEST ensure the software and instruments are working as designed?
Question 183
A security administrator is concerned about the increasing number of users who click on malicious links contained within phishing emails. Although the company has implemented a process to block these links at the network perimeter, many accounts are still becoming compromised. Which of the following should be implemented for further reduce the number of account compromises caused by remote users who click these links?
Question 184
A security engineer is analyzing an application during a security assessment to ensure it is configured to protect against common threats. Given the output below:
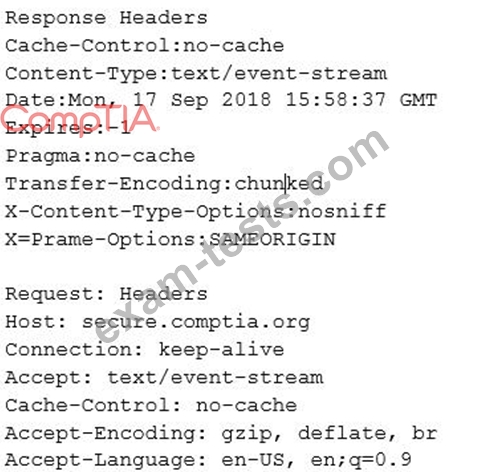
Which of the following tools did the security engineer MOST likely use to generate this output?

Which of the following tools did the security engineer MOST likely use to generate this output?
Question 185
The Chief information Officer (CIO) asks the system administrator to improve email security at the company based on the following requirements:
* Transaction being requested by unauthorized individuals.
* Complete discretion regarding client names, account numbers, and investment information.
* Malicious attackers using email to malware and ransomeware.
* Exfiltration of sensitive company information.
The cloud-based email solution will provide anti-malware reputation-based scanning, signature-based scanning, and sandboxing. Which of the following is the BEST option to resolve the boar's concerns for this email migration?
* Transaction being requested by unauthorized individuals.
* Complete discretion regarding client names, account numbers, and investment information.
* Malicious attackers using email to malware and ransomeware.
* Exfiltration of sensitive company information.
The cloud-based email solution will provide anti-malware reputation-based scanning, signature-based scanning, and sandboxing. Which of the following is the BEST option to resolve the boar's concerns for this email migration?

