Question 91
Legal counsel has notified the information security manager of a legal matter that will require the preservation of electronic records for 2000 sales force employees. Source records will be email, PC, network shares, and applications.
After all restrictions have been lifted, which of the following should the information manager review?
After all restrictions have been lifted, which of the following should the information manager review?
Question 92
A security analyst is reviewing the corporate MDM settings and notices some disabled settings, which consequently permit users to download programs from untrusted developers and manually install them. After some conversations, it is confirmed that these settings were disabled to support the internal development of mobile applications. The security analyst is now recommending that developers and testers have a separate device profile allowing this, and that the rest of the organization's users do not have the ability to manually download and install untrusted applications. Which of the following settings should be toggled to achieve the goal? (Choose two.)
Question 93
A network administrator is concerned about a particular server that is attacked occasionally from hosts on the Internet. The server is not critical; however, the attacks impact the rest of the network. While the company's current ISP is cost effective, the ISP is slow to respond to reported issues. The administrator needs to be able to mitigate the effects of an attack immediately without opening a trouble ticket with the ISP. The ISP is willing to accept a very small network route advertised with a particular BGP community string. Which of the following is the BESRT way for the administrator to mitigate the effects of these attacks?
Question 94
After investigating virus outbreaks that have cost the company $1,000 per incident, the company's Chief Information Security Officer (CISO) has been researching new antivirus software solutions to use and be fully supported for the next two years. The CISO has narrowed down the potential solutions to four candidates that meet all the company's performance and capability requirements:
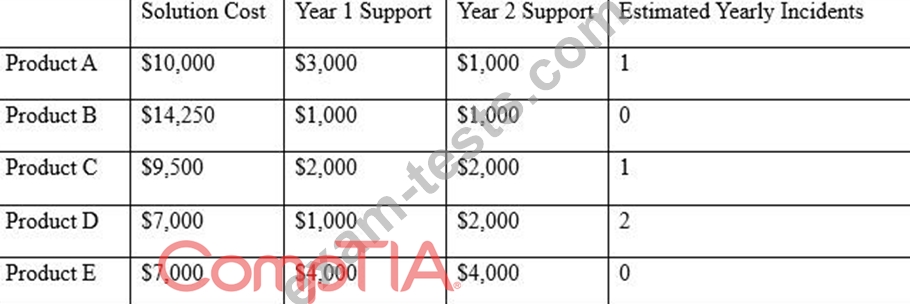
Using the table above, which of the following would be the BEST business-driven choice among five possible solutions?

Using the table above, which of the following would be the BEST business-driven choice among five possible solutions?
Question 95
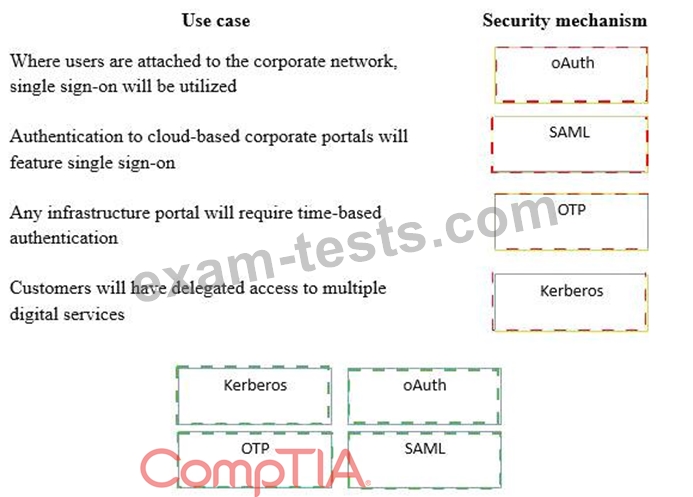
A security consultant is considering authentication options for a financial institution. The following authentication options are available. Drag and drop the security mechanism to the appropriate use case.
Options may be used once.
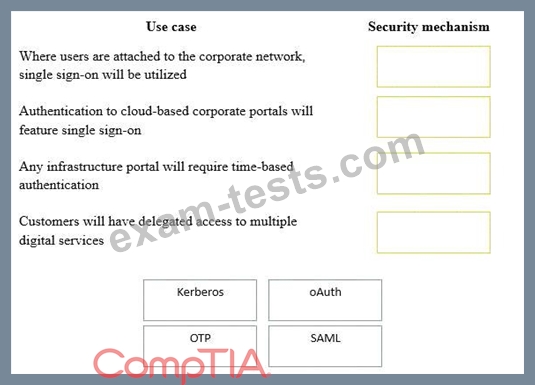
Options may be used once.