Question 1
A security engineer is helping the web developers assess a new corporate web application The application will be Internet facing so the engineer makes the following recommendation:
In an htaccess file or the site config add:
or add to the location block:
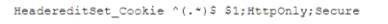
Which of the following is the security engineer trying to accomplish via cookies? (Select TWO)
In an htaccess file or the site config add:
or add to the location block:
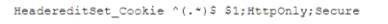
Which of the following is the security engineer trying to accomplish via cookies? (Select TWO)
Question 2
A company that has been breached multiple times is looking to protect cardholder data. The previous undetected attacks all mimicked normal administrative-type behavior. The company must deploy a host solution to meet the following requirements:
- Detect administrative actions
- Block unwanted MD5 hashes
- Provide alerts
- Stop exfiltration of cardholder data
Which of the following solutions would BEST meet these requirements? (Choose two.)
- Detect administrative actions
- Block unwanted MD5 hashes
- Provide alerts
- Stop exfiltration of cardholder data
Which of the following solutions would BEST meet these requirements? (Choose two.)
Question 3
An audit at a popular on-line shopping site reveals that a flaw in the website allows customers to purchase goods at a discounted rate.
To improve security the Chief Information Security Officer (CISO) has requested that the web based shopping cart application undergo testing to validate user input in both free form text fields and drop down boxes.
Which of the following is the BEST combination of tools and / or methods to use?
To improve security the Chief Information Security Officer (CISO) has requested that the web based shopping cart application undergo testing to validate user input in both free form text fields and drop down boxes.
Which of the following is the BEST combination of tools and / or methods to use?
Question 4
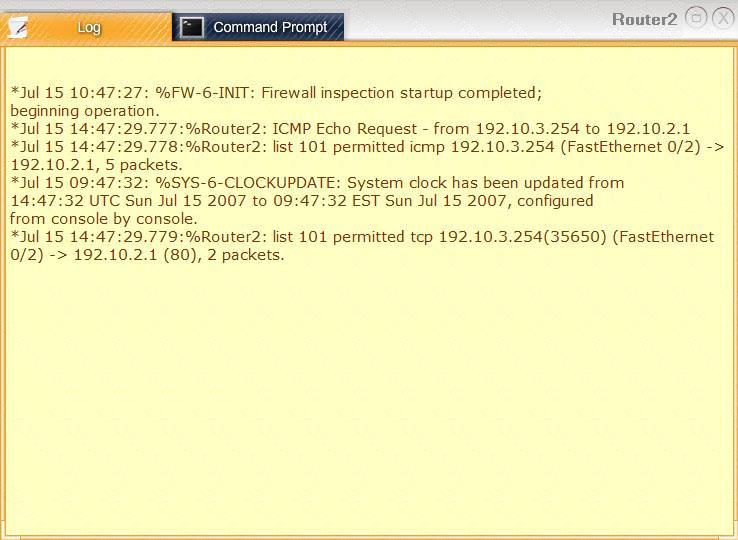
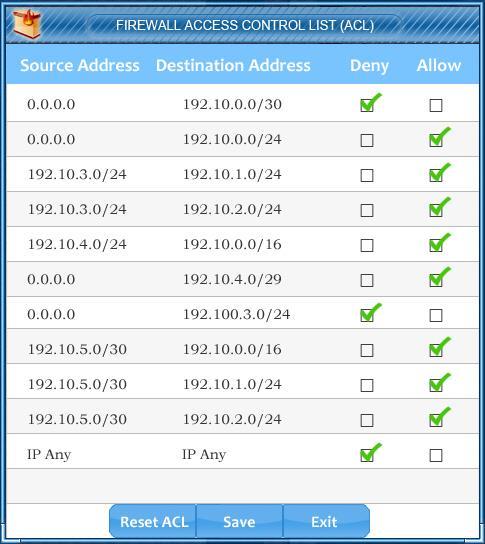
Company A has noticed abnormal behavior targeting their SQL server on the network from a rogue IP address.
The company uses the following internal IP address ranges: 192.10.1.0/24 for the corporate site and
192.10.2.0/24 for the remote site. The Telco router interface uses the 192.10.5.0/30 IP range.
Instructions: Click on the simulation button to refer to the Network Diagram for Company A.
Click on Router 1, Router 2, and the Firewall to evaluate and configure each device.
Task 1: Display and examine the logs and status of Router 1, Router 2, and Firewall interfaces.
Task 2: Reconfigure the appropriate devices to prevent the attacks from continuing to target the SQL server and other servers on the corporate network.
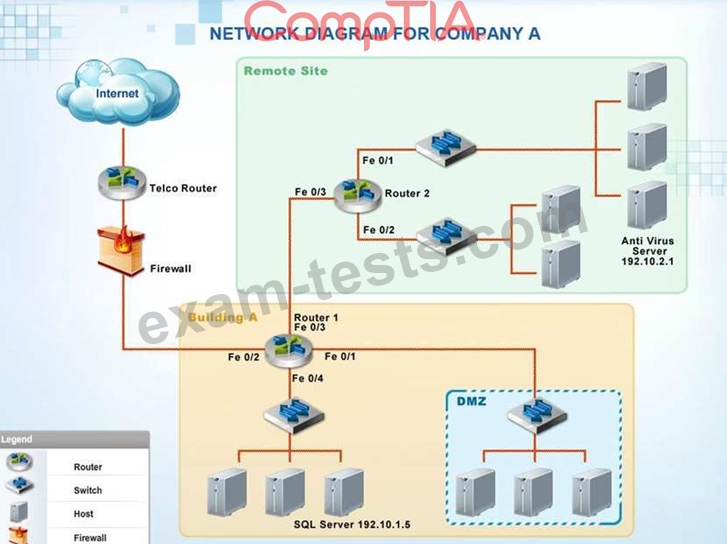
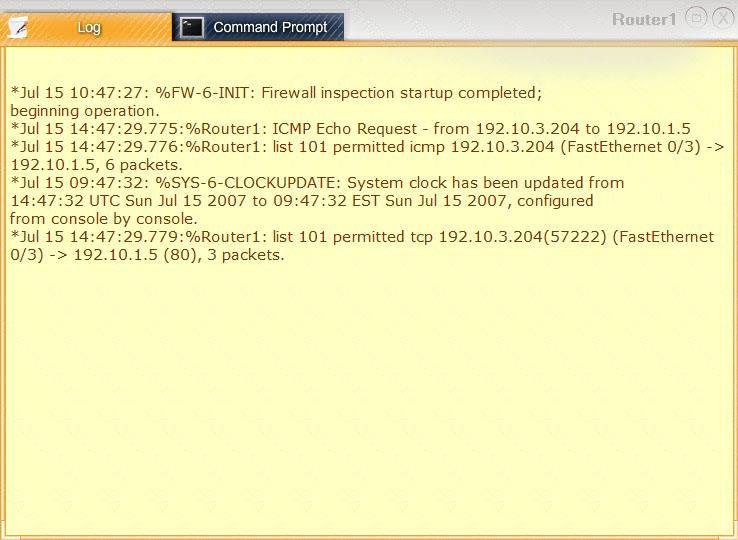
The company uses the following internal IP address ranges: 192.10.1.0/24 for the corporate site and
192.10.2.0/24 for the remote site. The Telco router interface uses the 192.10.5.0/30 IP range.
Instructions: Click on the simulation button to refer to the Network Diagram for Company A.
Click on Router 1, Router 2, and the Firewall to evaluate and configure each device.
Task 1: Display and examine the logs and status of Router 1, Router 2, and Firewall interfaces.
Task 2: Reconfigure the appropriate devices to prevent the attacks from continuing to target the SQL server and other servers on the corporate network.




Question 5
When reviewing KRIs of the email security appliance with the Chief Information Security Officer (CISO) of an insurance company, the security engineer notices the following:
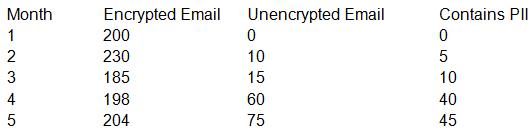
Which of the following measures should the security engineer take to ensure PII is not intercepted in transit while also preventing interruption to business?

Which of the following measures should the security engineer take to ensure PII is not intercepted in transit while also preventing interruption to business?

