Question 6
An attacker attempts to create a DoS event against the VoIP system of a company. The attacker uses a tool to flood the network with a large number of SIP INVITE traffic. Which of the following would be LEAST likely to thwart such an attack?
Question 7
Given the code snippet below:
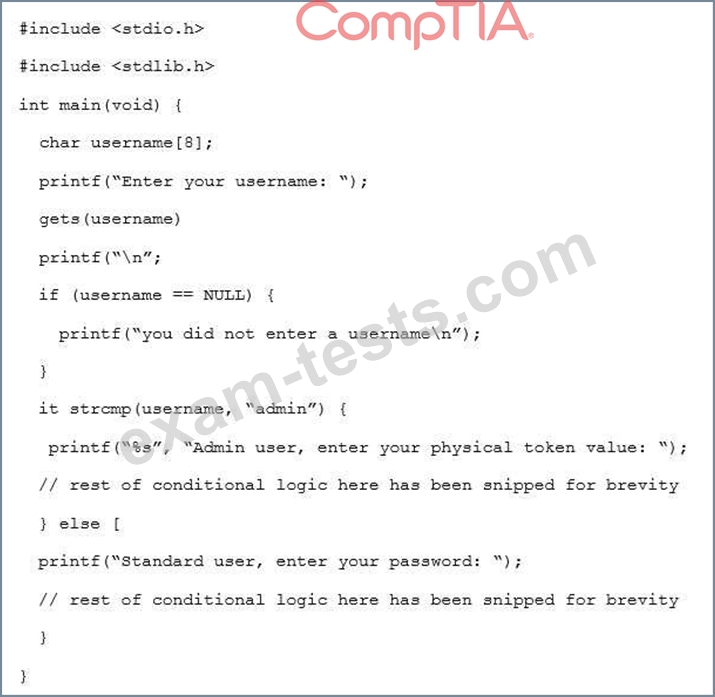
Which of the following vulnerability types in the MOST concerning?

Which of the following vulnerability types in the MOST concerning?
Question 8
A security analyst who is concerned about sensitive data exfiltration reviews the following:

Which of the following tools would allow the analyst to confirm if data exfiltration is occuring?

Which of the following tools would allow the analyst to confirm if data exfiltration is occuring?
Question 9
Given the code snippet below:

Which of the following vulnerability types in the MOST concerning?

Which of the following vulnerability types in the MOST concerning?
Question 10
A systems administrator receives an advisory email that a recently discovered exploit is being used in another country and the financial institutions have ceased operations while they find a way to respond to the attack. Which of the following BEST describes where the administrator should look to find information on the attack to determine if a response must be prepared for the systems? (Choose two.)
Premium Bundle
Newest CAS-003 Exam PDF Dumps shared by BraindumpsPass.com for Helping Passing CAS-003 Exam! BraindumpsPass.com now offer the updated CAS-003 exam dumps, the BraindumpsPass.com CAS-003 exam questions have been updated and answers have been corrected get the latest BraindumpsPass.com CAS-003 pdf dumps with Exam Engine here:

