Question 11
While the code is still in the development environment, a security architect is testing the code stored in the code repository to ensure the top ten OWASP secure coding practices are being followed. Which of the following code analyzers will produce the desired results?
Question 12
A network administrator with a company's NSP has received a CERT alert for targeted adversarial behavior at the company. In addition to the company's physical security, which of the following can the network administrator use to detect the presence of a malicious actor physically accessing the company's network or information systems from within?
(Select TWO).
(Select TWO).
Question 13
Given the following output from a security tool in Kali:


Question 14
Given the following:
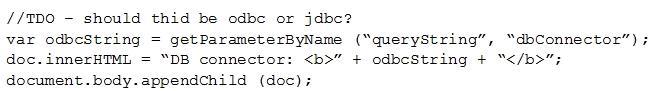
Which of the following vulnerabilities is present in the above code snippet?

Which of the following vulnerabilities is present in the above code snippet?
Question 15
A user workstation was infected with a new malware variant as a result of a drive-by download. The security administrator reviews key controls on the infected workstation and discovers the following:
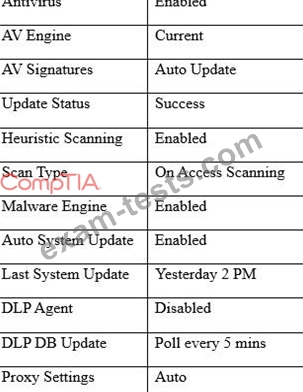
Which of the following would BEST prevent the problem from reoccurring in the future? (Choose two.)

Which of the following would BEST prevent the problem from reoccurring in the future? (Choose two.)
Premium Bundle
Newest CAS-003 Exam PDF Dumps shared by BraindumpsPass.com for Helping Passing CAS-003 Exam! BraindumpsPass.com now offer the updated CAS-003 exam dumps, the BraindumpsPass.com CAS-003 exam questions have been updated and answers have been corrected get the latest BraindumpsPass.com CAS-003 pdf dumps with Exam Engine here:

