Question 111
An administrator wants to enable policy based flexible mandatory access controls on an open source OS to prevent abnormal application modifications or executions. Which of the following would BEST accomplish this?
Question 112
Given the following:
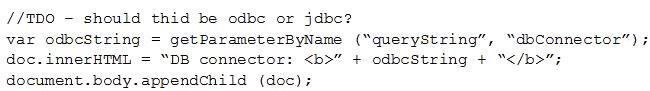
Which of the following vulnerabilities is present in the above code snippet?

Which of the following vulnerabilities is present in the above code snippet?
Question 113
An organization relies heavily on third-party mobile applications for official use within a BYOD deployment scheme. An excerpt from an approved text-based-chat client application AndroidManifest.xml is as follows:
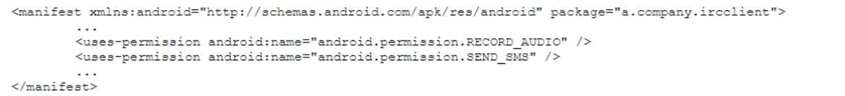
Which of the following would restrict application permissions while minimizing the impact to normal device operations?

Which of the following would restrict application permissions while minimizing the impact to normal device operations?
Question 114
A software development company lost customers recently because of a large number of software issues. These issues were related to integrity and availability defects, including buffer overflows, pointer deferences, and others. Which of the following should the company implement to improve code quality? (Select two).
Question 115
To prepare for an upcoming audit, the Chief Information Security Officer (CISO) asks for all 1200 vulnerabilities on production servers to be remediated. The security engineer must determine which vulnerabilities represent real threats that can be exploited so resources can be prioritized to migrate the most dangerous risks. The CISO wants the security engineer to act in the same manner as would an external threat, while using vulnerability scan results to prioritize any actions.
Which of the following approaches is described?
Which of the following approaches is described?

