Question 126
A hospital uses a legacy electronic medical record system that requires multicast for traffic between the application servers and databases on virtual hosts that support segments of the application. Following a switch upgrade, the electronic medical record is unavailable despite physical connectivity between the hypervisor and the storage being in place. The network team must enable multicast traffic to restore access to the electronic medical record. The ISM states that the network team must reduce the footprint of multicast traffic on the network.
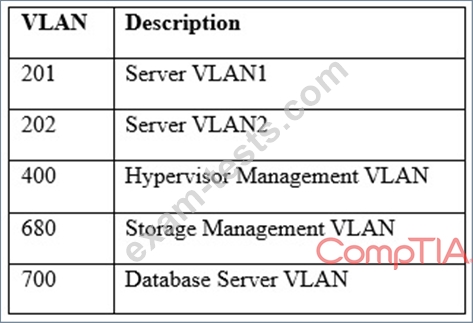
Using the above information, on which VLANs should multicast be enabled?

Using the above information, on which VLANs should multicast be enabled?
Question 127
A large hospital has implemented BYOD to allow doctors and specialists the ability to access patient medical records on their tablets. The doctors and specialists access patient records over the hospital's guest WiFi network which is isolated from the internal network with appropriate security controls. The patient records management system can be accessed from the guest network and require two factor authentication. Using a remote desktop type interface, the doctors and specialists can interact with the hospital's system. Cut and paste and printing functions are disabled to prevent the copying of data to BYOD devices. Which of the following are of MOST concern? (Select TWO).
Question 128
A company is the victim of a phishing and spear-phishing campaign Users are Clicking on website links that look like common bank sites and entering their credentials accidentally A security engineer decides to use a layered defense to prevent the phishing or lessen its impact Which of the following should the security engineer implement? (Select TWO)
Question 129
A security technician is incorporating the following requirements in an RFP for a new SIEM:
New security notifications must be dynamically implemented by the SIEM engine The SIEM must be able to identify traffic baseline anomalies Anonymous attack data from all customers must augment attack detection and risk scoring Based on the above requirements, which of the following should the SIEM support? (Choose two.)
New security notifications must be dynamically implemented by the SIEM engine The SIEM must be able to identify traffic baseline anomalies Anonymous attack data from all customers must augment attack detection and risk scoring Based on the above requirements, which of the following should the SIEM support? (Choose two.)
Question 130
A security analyst who is concerned about sensitive data exfiltration reviews the following:

Which of the following tools would allow the analyst to confirm if data exfiltration is occuring?

Which of the following tools would allow the analyst to confirm if data exfiltration is occuring?
Premium Bundle
Newest CAS-003 Exam PDF Dumps shared by BraindumpsPass.com for Helping Passing CAS-003 Exam! BraindumpsPass.com now offer the updated CAS-003 exam dumps, the BraindumpsPass.com CAS-003 exam questions have been updated and answers have been corrected get the latest BraindumpsPass.com CAS-003 pdf dumps with Exam Engine here:

