Question 131
A company wants to extend its help desk availability beyond business hours. The Chief Information Officer (CIO) decides to augment the help desk with a third-party service that will answer calls and provide Tier 1 problem resolution, such as password resets and remote assistance. The security administrator implements the following firewall change:
The administrator provides the appropriate path and credentials to the third-party company. Which of the following technologies is MOST likely being used to provide access to the third company?

The administrator provides the appropriate path and credentials to the third-party company. Which of the following technologies is MOST likely being used to provide access to the third company?
Question 132
Company leadership believes employees are experiencing an increased number of cyber attacks; however, the metrics do not show this. Currently, the company uses "Number of successful phishing attacks" as a KRI, but it does not show an increase.
Which of the following additional information should be the Chief Information Security Officer (CISO) include in the report?
Which of the following additional information should be the Chief Information Security Officer (CISO) include in the report?
Question 133
A system integrator wants to assess the security of the application binaries delivered by its subcontracted vendors. The vendors do not deliver source code as a part of their contract Which of the Mowing techniques can the integrator use to accomplish the objective? (Select TWO)
Question 134
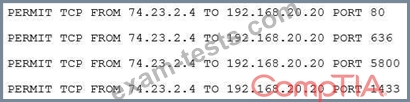
A systems administrator has installed a disk wiping utility on all computers across the organization and configured it to perform a seven-pass wipe and an additional pass to overwrite the disk with zeros. The company has also instituted a policy that requires users to erase files containing sensitive information when they are no longer needed.
To ensure the process provides the intended results, an auditor reviews the following content from a randomly selected decommissioned hard disk:

Which of the following should be included in the auditor's report based in the above findings?
To ensure the process provides the intended results, an auditor reviews the following content from a randomly selected decommissioned hard disk:

Which of the following should be included in the auditor's report based in the above findings?
Question 135
During a recent audit of servers, a company discovered that a network administrator, who required remote access, had deployed an unauthorized remote access application that communicated over common ports already allowed through the firewall. A network scan showed that this remote access application had already been installed on one third of the servers in the company. Which of the following is the MOST appropriate action that the company should take to provide a more appropriate solution?

