Question 296
select id, firstname, lastname from authors
User input= firstname= Hack;man
lastname=Johnson
Which of the following types of attacks is the user attempting?
User input= firstname= Hack;man
lastname=Johnson
Which of the following types of attacks is the user attempting?
Question 297
An organization has hardened its end points m the following ways
* USB ports are disabled except for approved input device IDs (e.g, mouse, keyboard)
* A desktop firewall is Mocking all outbound network connections, except to approved internal systems
* A VPN client is the only way to connect to the corporate network remotely and split tunneling is disabled
* Bluetooth is disabled
* Web browsing from end points is permitted but the traffic is directed through the VPN to the corporate gateway
* The email client is permitted to connect to the internal server over the VPN and DLP rules prohibit sending sensitive information to external recipients The organization recently suffered a security breach which a file containing PlI somehow made it from a remote user's laptop to an unauthorized host Which of the following is the MOST likely for how (his happened?
* USB ports are disabled except for approved input device IDs (e.g, mouse, keyboard)
* A desktop firewall is Mocking all outbound network connections, except to approved internal systems
* A VPN client is the only way to connect to the corporate network remotely and split tunneling is disabled
* Bluetooth is disabled
* Web browsing from end points is permitted but the traffic is directed through the VPN to the corporate gateway
* The email client is permitted to connect to the internal server over the VPN and DLP rules prohibit sending sensitive information to external recipients The organization recently suffered a security breach which a file containing PlI somehow made it from a remote user's laptop to an unauthorized host Which of the following is the MOST likely for how (his happened?
Question 298
Joe, a penetration tester, is tasked with testing the security robustness of the protocol between a mobile web application and a RESTful application server. Which of the following security tools would be required to assess the security between the mobile web application and the RESTful application server? (Select TWO).
Question 299
A university's help desk is receiving reports that Internet access on campus is not functioning. The network administrator looks at the management tools and sees the 1Gbps Internet is completely saturated with ingress traffic. The administrator sees the following output on the Internet router:
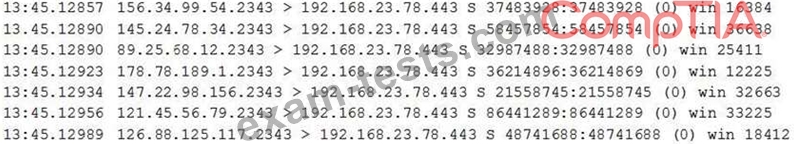
The administrator calls the university's ISP for assistance, but it takes more than four hours to speak to a network engineer who can resolve the problem. Based on the information above, which of the following should the ISP engineer do to resolve the issue?

The administrator calls the university's ISP for assistance, but it takes more than four hours to speak to a network engineer who can resolve the problem. Based on the information above, which of the following should the ISP engineer do to resolve the issue?
Question 300
A user is suspected of engaging in potentially illegal activities. Law enforcement has requested that the user continue to operate on the network as normal. However, they would like to have a copy of any communications from the user involving certain key terms.
Additionally, the law enforcement agency has requested that the user's ongoing communication be retained in the user's account for future investigations. Which of the following will BEST meet the goals of law enforcement?
Additionally, the law enforcement agency has requested that the user's ongoing communication be retained in the user's account for future investigations. Which of the following will BEST meet the goals of law enforcement?

