Question 301
Which of the following is the BEST way for a company to begin understanding product-based solutions to mitigate a known risk?
Question 302
During a sprint, developers are responsible for ensuring the expected outcome of a change is thoroughly evaluated for any security impacts. Any impacts must be reported to the team lead. Before changes are made to the source code, which of the following MUST be performed to provide the required information to the team lead?
Question 303
The finance department has started to use a new payment system that requires strict PII security restrictions on various network devices. The company decides to enforce the restrictions and configure all devices appropriately. Which of the following risk response strategies is being used?
Question 304
The SOC has noticed an unusual volume of traffic coming from an open WiFi guest network that appears correlated with a broader network slowdown The network team is unavailable to capture traffic but logs from network services are available
* No users have authenticated recently through the guest network's captive portal
* DDoS mitigation systems are not alerting
* DNS resolver logs show some very long domain names
Which of the following is the BEST step for a security analyst to take next?
* No users have authenticated recently through the guest network's captive portal
* DDoS mitigation systems are not alerting
* DNS resolver logs show some very long domain names
Which of the following is the BEST step for a security analyst to take next?
Question 305
An internal penetration tester was assessing a recruiting page for potential issues before it was pushed to the production website. The penetration tester discovers an issue that must be corrected before the page goes live. The web host administrator collects the log files below and gives them to the development team so improvements can be made to the security design of the website.
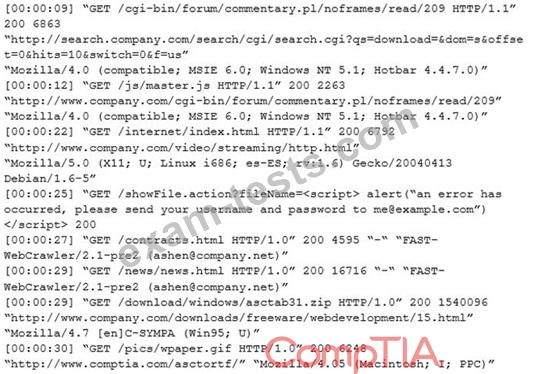
Which of the following types of attack vector did the penetration tester use?

Which of the following types of attack vector did the penetration tester use?

