Question 361
A cybersecurity analyst is conducting packet analysis on the following:
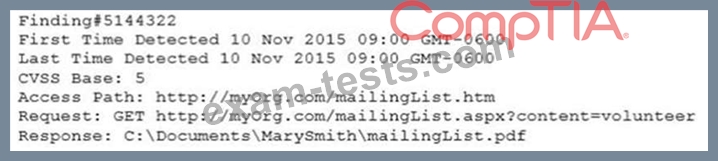
Which of the following is occurring in the given packet capture?

Which of the following is occurring in the given packet capture?
Question 362
A security researcher is gathering information about a recent spoke in the number of targeted attacks against multinational banks. The spike is on top of already sustained attacks against the banks. Some of the previous attacks have resulted in the loss of sensitive data, but as of yet the attackers have not successfully stolen any funds.
Based on the information available to the researcher, which of the following is the MOST likely threat profile?
Based on the information available to the researcher, which of the following is the MOST likely threat profile?
Question 363
A cloud architect needs to isolate the most sensitive portion of the network while maintaining hosting in a public cloud Which of the following configurations can be employed to support this effort?
Question 364
An application present on the majority of an organization's 1,000 systems is vulnerable to a buffer overflow attack. Which of the following is the MOST comprehensive way to resolve the issue?
Question 365
A security analyst has been asked to create a list of external IT security concerns, which are applicable to the organization. The intent is to show the different types of external actors, their attack vectors, and the types of vulnerabilities that would cause business impact. The Chief Information Security Officer (CISO) will then present this list to the board to request funding for controls in areas that have insufficient coverage.
Which of the following exercise types should the analyst perform?
Which of the following exercise types should the analyst perform?

