Question 436
After the departure of a developer under unpleasant circumstances, the company is concerned about the security of the software to which the developer has access. Which of the following is the BEST way to ensure security of the code following the incident?
Question 437
A database administrator is required to adhere to and implement privacy principles when executing daily
tasks. A manager directs the administrator to reduce the number of unique instances of PII stored within an
organization's systems to the greatest extent possible.
Which of the following principles is being demonstrated?
tasks. A manager directs the administrator to reduce the number of unique instances of PII stored within an
organization's systems to the greatest extent possible.
Which of the following principles is being demonstrated?
Question 438
Following the merger of two large companies the newly combined security team is overwhelmed by the volume of logs flowing from the IT systems The company's data retention schedule complicates the issue by requiring detailed logs to be collected and available for months Which of the following designs BEST meets the company's security and retention requirement?
Question 439
A hospital is using a functional magnetic resonance imaging (fMRI) scanner, which is controlled legacy desktop connected to the network. The manufacturer of the fMRI will not support patching of the legacy system. The legacy desktop needs to be network accessible on TCP port 445 A security administrator is concerned the legacy system will be vulnerable to exploits Which of the following would be the BEST strategy to reduce the risk of an outage while still providing for security?
Question 440
A user workstation was infected with a new malware variant as a result of a drive-by download. The security administrator reviews key controls on the infected workstation and discovers the following:
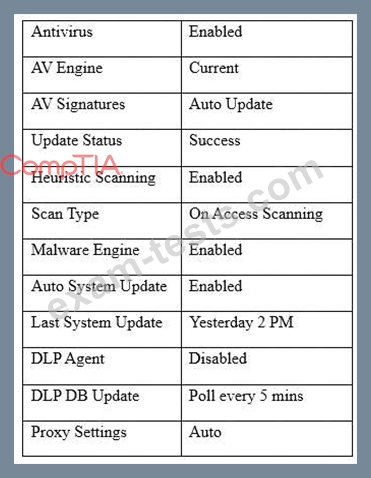
Which of the following would BEST prevent the problem from reoccurring in the future? (Choose two.)

Which of the following would BEST prevent the problem from reoccurring in the future? (Choose two.)
Premium Bundle
Newest CAS-003 Exam PDF Dumps shared by BraindumpsPass.com for Helping Passing CAS-003 Exam! BraindumpsPass.com now offer the updated CAS-003 exam dumps, the BraindumpsPass.com CAS-003 exam questions have been updated and answers have been corrected get the latest BraindumpsPass.com CAS-003 pdf dumps with Exam Engine here:

